Throughout my investigations into phishing and malicious scripts, I am constantly seeing the malicious actors uploading additional scripts such as the leaf mailer (will be an article on this later on) and various web shells. One of the most common web shells still being used today is the ‘Web shell by orb’ or known as WSO, The WSO shell has been around before 2010 with reports of the web shell showing up in 2009, The default screen for WSO is a file manager with a range of buttons that allow additional features.
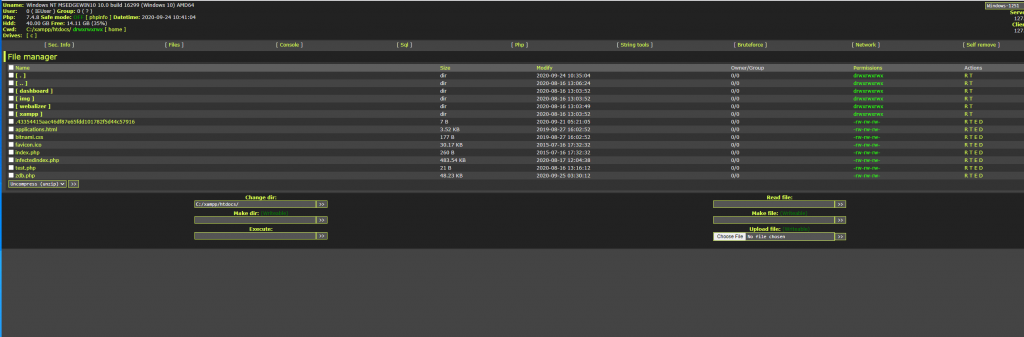
Under the Sec.info tab, you are presented with information about the host itself and what PHP functions are disabled. The disabled functions are important as it can limit the access the web shell has and what it can do.
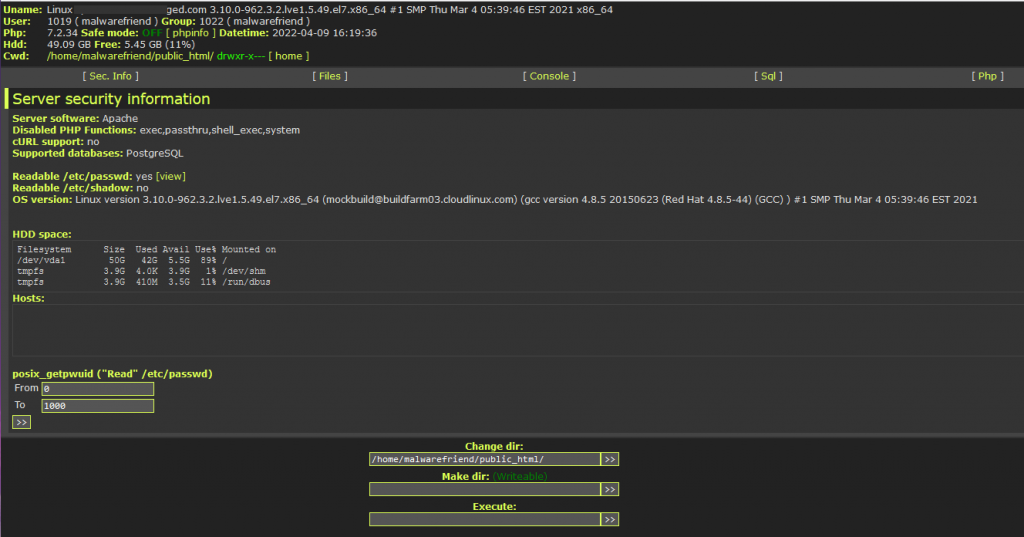
the console tab will give you direct terminal access to the account which will allow the malicious actor to run scripts and commands on the hosting environment.
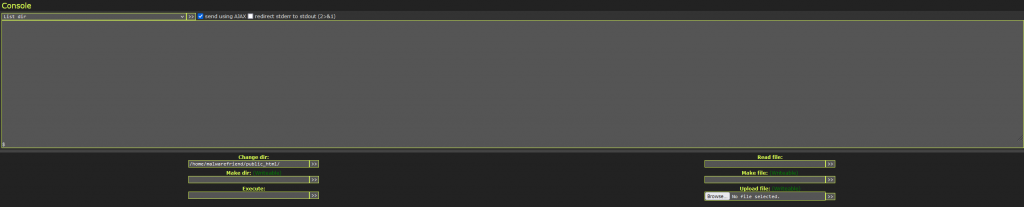
With the SQL tab you have the ability to browse the database as long as you have database credentials. The credentials can be obtained by reading the configuration file of the content management system.
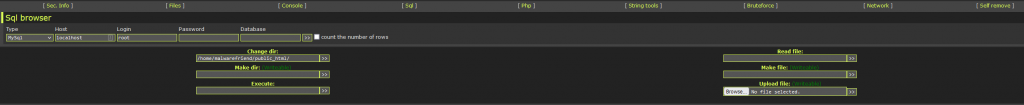
Like the console tab WSO provides you with a direct PHP compiler that will let you compile any PHP scripts or code,
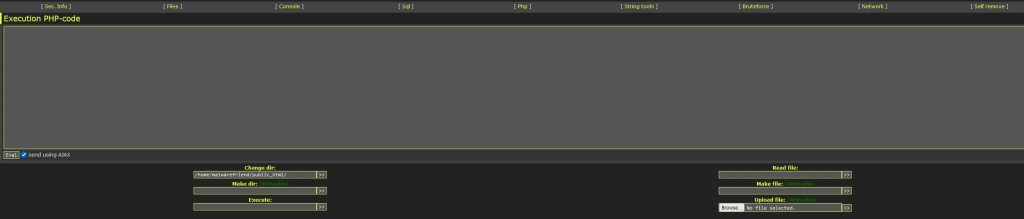
You also have a strings tab. This tab is used to encode strings into various encodings, This is used for hiding malicious code in the hopes to avoid Web application firewalls and scanners.
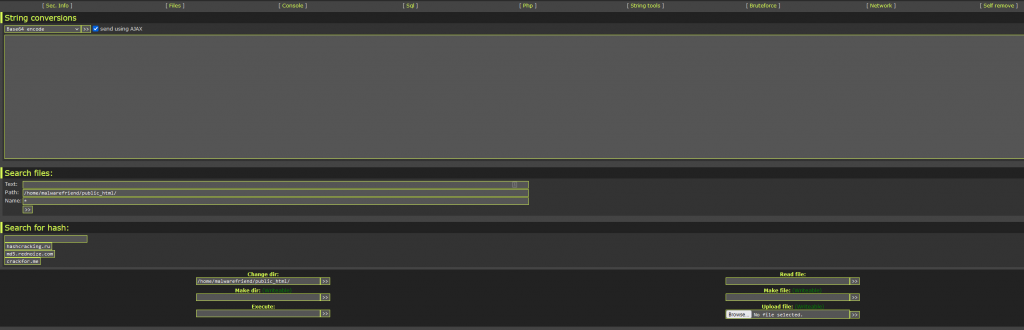
You have a brute force tool, With most servers they have some sort of Firewall that would detect inbound brute force and block the attack from happening. With a tool like this, you could launch a brute-force internally and attempt to crack passwords this way.
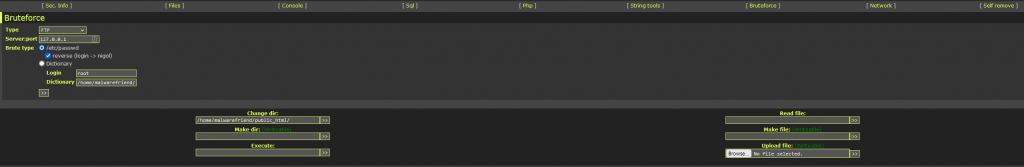
and finally, a network tool that allows you to setup persistence to an external environment or a command and control server
As with all these features you can see why the WSO is still one of the most commonly used web shells being used.
I have tracked the Web shell being uploaded in a few different formats and with different encoding methods. The most common I have seen is the web shell encoded via Base64 and then compressed using Gunzip (GZ), Below is a sample of code that is hiding WSO.


Once decoded some of the telltale signs you are working with WSO. Please note not all of the samples below exist in the same script.
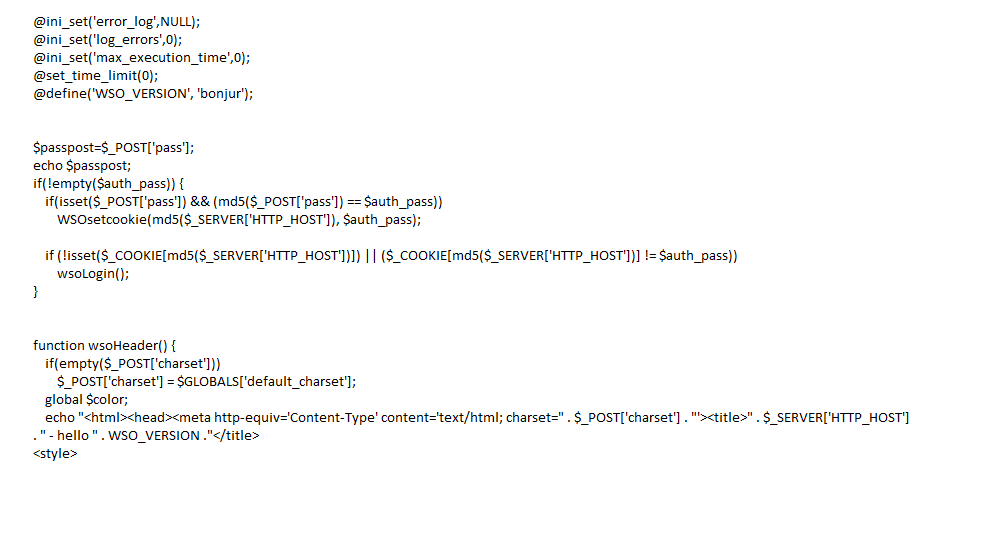
Another reason why many malicious actors like using WSO is the ability to password-protect their backdoor onto a victim’s server. You will find once a hacker has exploited a vulnerability and imbedded their own web shell they will go ahead and patch the vulnerability to prevent others from following their steps
The password protection works by using a simple HTTP password authentication. Sometimes you’re lucky to find the password is listed in the source code as you can see in the example below
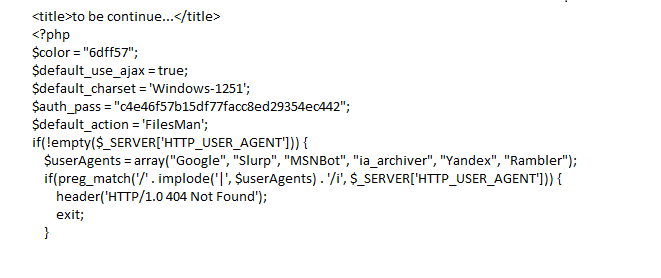
As mentioned above the malicious action would use an existing vulnerability to upload the source code of the shell to an existing file. Once they have the code embedded they have full access to the user that is running as the webserver.
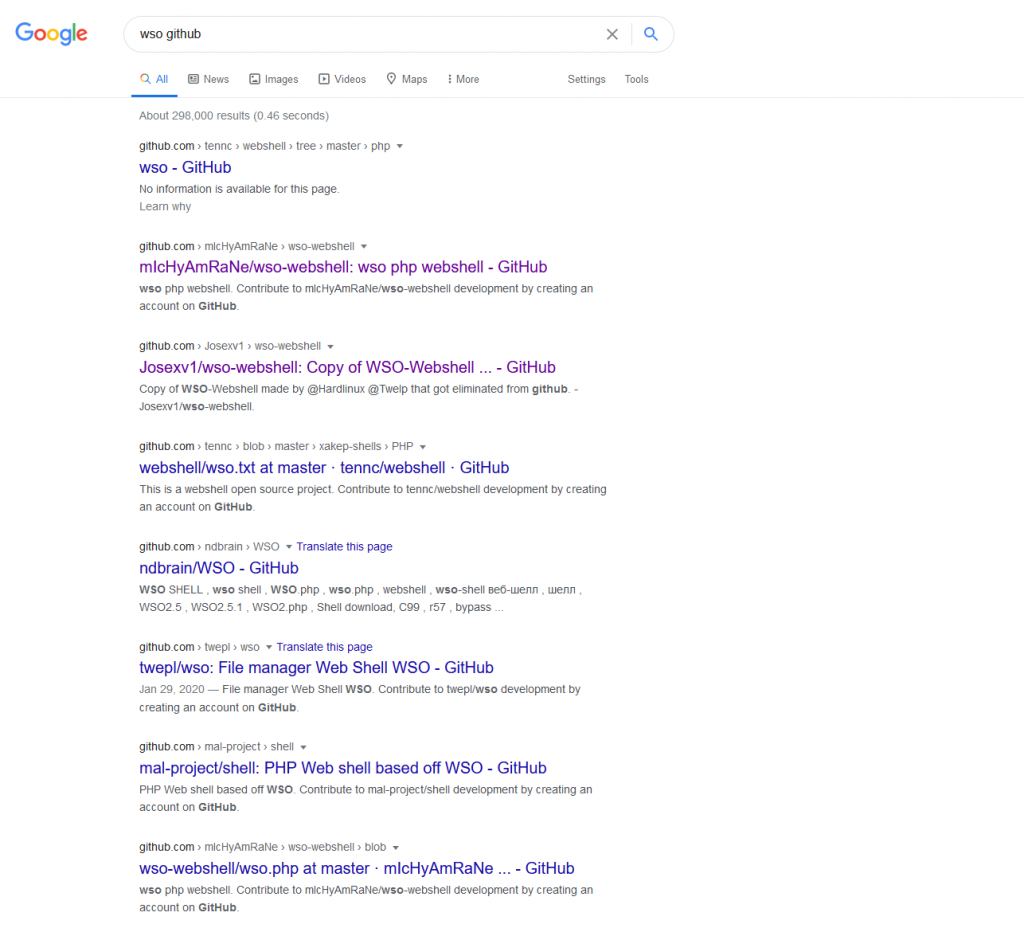
Original reports had the web shell showing up in 2009 (Source: https://www.getastra.com/e/malware/infections/wso-shell-most-popular-malicious-tool-used-by-hackers) and was shared on a Russian forum since then there are a few variations of WSO being shared on the web. This is demonstrated by simply searching for ‘wso GitHub
WSO is also listed as a PHP backdoor in VirusTotal. If you also run ConfigServe Exploit scanner it is detected and quarantined before the script can be used to exploit the environment. In the example below I was analyzing the zdb.php file which is one of the variants of the WSO script I discussed above. The source code was detected by 16 different Antivirus programs.
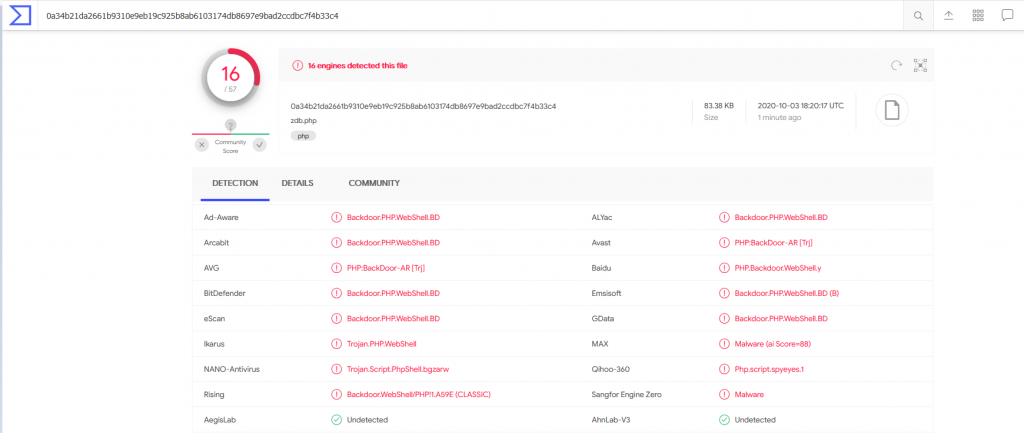
As more and more people continue to use the WSO web shell we are seeing the hash signature constantly changing to stay ahead of the antiviruses and malware scanners, It is a bit like whack-a-mole as new variations are being developed daily. If you ever encounter a web shell in your environment it is recommended that you remove the shell as soon as possible and rotate any passwords such as database connection strings.